Are you ready to fight?
Jedimaster: We can’t afford to wait any longer. Energy I’ll use to defeat their spaceships and clear the way for our troops.
Just me give a figher
Summary: packet analyze, a little reverse
Program is a x86 ELF file. Size of file is 8367 K. At first glance it is too large for reverse analyze and also in challenge describe we can find a “hint”:
(hint: no, it’s not a virus. Just run it and see what happens!)
Ok, just do it! And after start the program we see that it is a game!
And on the condition you get a flag if you type 100 000 pts. So many! It will take half of life =)
Also in the condition you will find that you can win only if you play online! It is the point! Lets run wireshark and look:
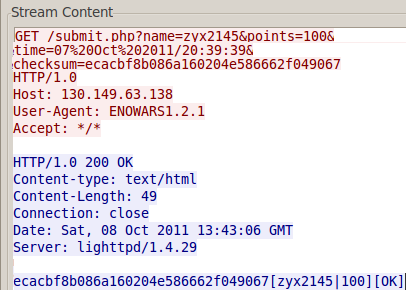 So when game finish it sends a GET request to 130.149.63.138 with User-Agent = ENOWARS.2.1 and fields:
So when game finish it sends a GET request to 130.149.63.138 with User-Agent = ENOWARS.2.1 and fields:
- name – we type it before start a game
- points – value of our points
- time – current time
- checksum – WTF?
It would have been easy to send request with fake points and get a real flag, if field “checksum” hadn’t been here.
If we send request with incorrect checksum we will get error:
7B185C9BA825D442197CD35F5AC26C0Fchecksum failed: zyx2145|100000|19 Jul 2011/05:27:16
But in this error we will find a hint! Checksum is calculated by field: name, points, time
So checksum looks like md5 and we can check it. For that we can just find “migic” number in program:
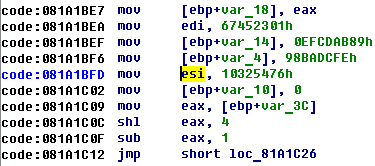 It looks like md5 init function =)
It looks like md5 init function =)
After several attempts we found correct md5 for data from first request (with correct data but only 10 points).
Last part is easiest one! Let’s calculate md5 for request data with a lot of points:
name points time (without space):
Smoked and Leet
10000000000000000000000000000000000000000000000000000000
19 Jul 2011/05:27:16
MD5 = F973CE7254C70F76551C6B1B80419847
Command line:
wget –user-agent=ENOWARS1.2.1
“http://130.149.63.138//submit.php?name=Smoked and Leet&
points=100000000000000000000000000000000000000000000000000&
time=19 Jul 2011/05:27:16&checksum=f973ce7254c70f76551c6b1b80419847”
Result:
f973ce7254c70f76551c6b1b80419847
[Smoked and Leet
|10000000000000000000000000000000000000000000000000000000|
eno49e24cedf5ba266ab3404b888cc8bc2f34609]][OK]
Flag: eno49e24cedf5ba266ab3404b888cc8bc2f34609
and honor!


1 comment
I’m going with another way. OOP binary takes hour for finding 81ae50b – place for patching. Another things that hash not correctly shown at game, so 10 min more for getting full length key.
Find Crypto really hepls you with this task.