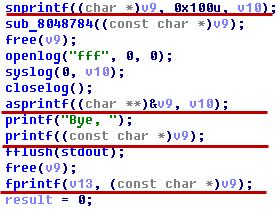
After examining some code retrieved by our operative we are unsure whether it was written by an evil genius or a google employee. We will let you decide. Summary: linux x64 binary, obfuscated xor
Tag: pctf
May 01
PlaidCTF 2012 – RSA [200] (Password Guessing)
We recently intercepted a plethora of robot transmissions but they are all encrypted with some strange scheme we just can’t quite figure out. Can you crack it? Summary: small public exponent: 3
May 01
PlaidCTF 2012 – Encryption Service [300] (Password Guessing)
We found the source code for this robot encryption service, except the key was redacted from it. The service is currently running at 23.21.15.166:4433 Summary: IV predict, byte-by-byte bruteforce
May 01
PlaidCTF 2012 – Nuclear Launch Detected [150] (Password Guessing)
Our spies intercepted communications and a file between 5 of the top 10 robo-generals and their nuclear bomb server. We must recover the final launch code from the 5 robo-general’s secret codes, so we can stop the detonation! Summary: Shamir’s Secret Sharing
May 01
PlaidCTF 2012 – Format [99] (Pwnables)
Up on a hill, far away, sits the robot king of old. While he was once great, he recently has seemed to just offer simple challenges. Vanquish him and bring honor to your team! Summary: rand guessing, format string exploitation
Apr 27
PlaidCTF 2011 #23 – Exploit Me :p (200)
Category: pwnables It seems like AED also has some plans to raise hacker force! We found this binary as an exploitation practice program in the office, but they forgot to remove the setgid flag on the program. So we can get the secret key! ssh username@a5.amalgamated.biz Username: exp_1 Password: jNKpzFuRLpsIW9xzqNIpCVF1 Summary: .dynamic->FINI overwriting, execl symlink …
Apr 27
PlaidCTF 2011 #19 – Another small bug (250)
Category: pwnables This time, let’s attack /opt/pctf/z2/exploitme. ssh username@a5.amalgamated.biz Username: z2_1 Password: 29rpJinvpwoI7pzdufQc4h6edzvyh Summary: buffer overflow, static binary binary
Apr 27
PlaidCTF 2011 #18 – A small bug (250)
Category: pwnables Get access to the key using /opt/pctf/z1/exploitme. ssh username@a5.amalgamated.biz Username: z1_1 Password: GwB4eivw9NTvCjmobw1EnuyqcWfJs Summary: race condition, create a symlink before the file is opened binary
Apr 26
PlaidCTF 2011 #24 – Calculator (200)
Category: pwnables AED’s summer internship program is notorious for attracting terrible programmers. They’ve resorted to giving them some of the simplest projects to work on. We expect this service that the latest ‘All-Star’ intern worked on all summer is no where near secure. nc a9.amalgamated.biz 60124 Summary: python eval with some filtering
Apr 26
PlaidCTF 2011 #20 – C++ upgrade (300)
Category: pwnables They have an update for the vulnerable C++ program trying to fix the bug. However, the coders at AED suck and introduced another stupid mistake. Get a shell (and the key, too.) ssh username@a5.amalgamated.biz Username: cpp2_1 Password: zKQaKrdFPSsT6j03XSt31NaT0H Summary: tricky overflow class’ method and exec’ing symlinks binary
Apr 26
PlaidCTF 2011 #17 – C++5x (300)
Category: pwnables AED decided to use C++ to develop their internal tools. However, they seem to make a mistake one of their new C++ programs. Exploit and get the key! ssh username@a5.amalgamated.biz Username: cpp1_1 Password: IwKheuEHvR1jYXmjIYz8bo8FFe1h8 Summary: tricky overflow class’ method and exec’ing symlinks binary
Apr 26
PlaidCTF 2011 #25 – PC Rogue (600)
Category: pwnables Amalgamated has banned the use of Solitaire due to loss of productivity. The only employee who would write a new game for everyone only likes ‘retro’ games, and has placed a text-adventure version of pacman on a company server. We don’t believe he could have coded this securely, and the server contains a …