The Plague is building an army of evil hackers, and they are starting off by teaching them python with this simple service. Maybe if you could get full access to this system, at 54.196.37.47:9990, you would be able to find out more about The Plague’s evil plans. Code: (can be run locally with $ socat …
Tag: x64
Jun 17
Defcon CTF Quals 2013 – \xff\xe4\xcc 4 (penser)
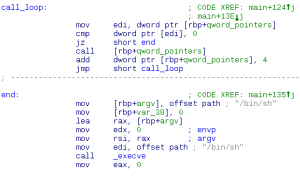
good luck. penser.shallweplayaga.me:8273 http://assets-2013.legitbs.net/liabilities/penser Download penser binary » Summary: x86_64 Unicode-proof shellcoding.
Oct 25
Hack.lu 2012 CTF Challenge #14-15 (150+250)
14 – Safehouse It’s the middle of the night. Nothing but complete darkness and the moaing of approaching zombies surrounds you. You need to escape. Fast. There seems to be nothing to hide and nowhere to run. But then – a small dancing gleam appears while you are running through the blackness. Could it be? …
May 01
SIMD [250] (Pirating)
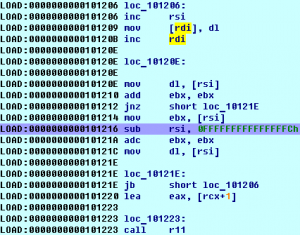
After examining some code retrieved by our operative we are unsure whether it was written by an evil genius or a google employee. We will let you decide. Summary: linux x64 binary, obfuscated xor
Apr 30
PlaidCTF 2012 – Bouncer [250] (Practical Packets)
In a recent battle we took an enemy robot hostage and examined his operating system. During the examination we found a piece of robot malware that we don’t quite understand. Can you enumerate its targets? This challenge was made by our friends at ManTech. If you enjoyed it, you might be interested in working for them. Summary: unpack …