Heading up the steeple gave you and your companion a nice view over the outbreak situation in your city. But it also attracted a lot of unwanted attention. Zombies are surrounding your spot and are looking for an entrance to the building. You obviously need some bait to lure them away so you can flee safely. Solve this challenge to find out which human bodypart zombies like the most. https://ctf.fluxfingers.net/challenges/mealtime.exe
Summary: reverse engineering, TEA crypto, anti -debuging
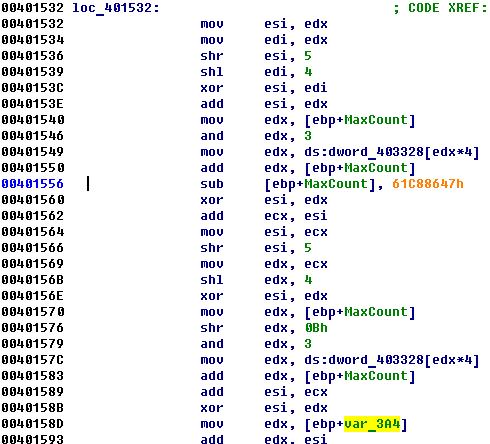
The given file is non-packed PE x86. If you try to execute the program it will crash. (I think it is bad style for CTF when a program crashes even without a debugger). The program consists of a lot of anti-debugger tricks, and it is quite annoying to analyze because you never know why it crashed (anti debugger or just by design). So, I had decided to analyze it only statically and soon found few parts of the program which could be interesting. These parts are crypto TEA algorithm:
So, the further analysis was quite easy: I get all encrypted data and keys from the program and decrypted them:
#include <stdio.h> #define uint32_t unsigned int void tea_decrypt (uint32_t* buff, uint32_t* keys) { uint32_t sum = 0xC6EF3720, delta = 0x61C88647; /* set up */ for (int i = 0; i < 32; i++) { buff[1] -= (((buff[0] << 4)^(buff[0] >> 5)) + buff[0]) ^ (sum + keys[(sum >> 11) & 3]); sum += delta; buff[0] -= (((buff[1] << 4)^(buff[1] >> 5)) + buff[1]) ^ (sum + keys[sum & 3]); } } void main() { uint32_t key3[] = { 0x31216674, 0x31216674, 0x31216674, 0x31216674 }; uint32_t key2[] = { 0x63737265, 0x63737265, 0x63737265, 0x63737265 }; uint32_t key1[] = { 0x676E6966, 0x676E6966, 0x676E6966, 0x676E6966 }; uint32_t key0[] = { 0x78756C66, 0x78756C66, 0x78756C66, 0x78756C66 }; uint32_t buff[] = { 0x4FA2D1F6, 0x3D6906FC, 0x80AF74A4, 0xDD9CDC44, 0x131AF1BE, 0x4BB34049, 0x904A05D2, 0xDA4C7A90, 0}; tea_decrypt (buff, key0); tea_decrypt (&buff[2], key1); tea_decrypt (&buff[4], key2); tea_decrypt (&buff[6], key3); printf("%s", buff); } |
The flag is –delicious_brainz_are_delicious

2 comments
1 ping
nice work but how did you get this sum = 0xC6EF3720 ?
Author
It is a standard variable for the TEA algorithm.
[…] http://leetmore.ctf.su/wp/hack-lu-2012-ctf-challenge-25-200/?utm_campaign=ctftime (貌似需要翻墙) […]