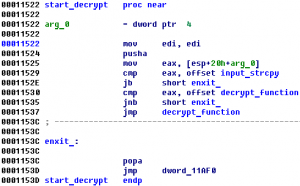
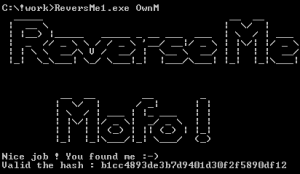
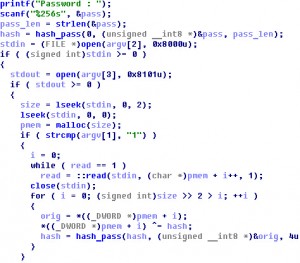
Category: reversing binary Summary: hash algorithm analyze, crackme
Category: Writeups
Sep 25
hack.lu CTF 2011 FluxScience (450)
Category: reversing Thanks to a former employee of FluxScience (one of our competitors), we managed to get hands on some important files which might help us revealing company secrets. Attached you will find the files. The employee who provided them got fired. You might be lucky and find his account still working: FLUX-38B273DD75860083-0B3DD6B02EC5B9B1-4AFFBAC2EB8B4D17 He might …
Sep 22
hack.lu CTF 2011 Wipe out the Klingons (400)
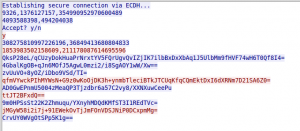
Category: crypto We already made it. The evil Klingons agression is nearly fended. But their final mothership is well protected and even sacrifing a huge number of battleships caused only minor damage. Spies told us an unclear message caused most technical operators and the commander to leave the ship. Unfortunately we are unable to locate …
Sep 21
hack.lu CTF 2011 Spy Aboard! (300)
Category: crypto We have a spy aboard! For around 5 minutes ago we intercepted an encrypted transmission to an enemy outpost. It seems like we interrupted the mole in the act because we found an open transmission program on our terminals. We are 100% sure that he sent the position of our fleet to the …
Sep 21
hack.lu CTF 2011 Simplexor (200)
Category: crypto To get a better security we deceided to encrypt our most secret document with the secure xor-algorithm. Unfortunately we lost the key. Now we are sad. Can you help us recovering the key? Download Summary: recovering multibyte xor-key, using autocorrelation
Sep 21
hack.lu CTF 2011 Antique Space Shuttle (300)
Category: exploiting Your command is to get as much information about the crew of an antique space shuttle. We know our acient father used finger as reference point at nc ctf.hack.lu 2003 Summary: bash injection, and buffer overflow on a suid binary to get more privilegies
Sep 21
hack.lu CTF 2011 Space Station 0xB321054A (300)
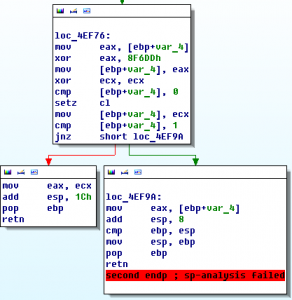
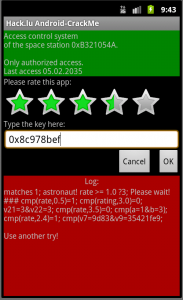
Category: exploiting You have seen a deserted space station. Your task is to enter it. The first barrier is the access system. But you can find a module with the application on it. Here is the file: download What is the key? (There is also station A, but station B is the advanced one.) Summary: …
Sep 13
DEFCON 19 Final – hiver
This challenge was on logic and understanding of the bloom filter. The binary is for FreeBSD. binary Summary: understanding of the bloom filter, bruteforce bloom filter set.
Sep 13
DEFCON 19 Final – forgetu
This challenge was on remote exploiting. The binary is for FreeBSD. binary Summary: bruteforce password, buffer overflow, jump to shellcode
Jul 25
NdH2k11 WaRgam3 – CrackMe 400 (2000pts). Part 2
It is second part of CrackMe task describing. First one you can find there In this part I will detail the analysis of driver ReverMe1.sys
Jul 24
NdH2k11 WaRgam3 – CrackMe 400 (2000pts). Part 1
This challenge was on reverse engineering. The binary is 32bit MZ-PE executable for Windows. binary Summary: reverse engineering, crypto
Jul 23
NdH2k11 WaRgam3 – CrackMe 100 (500pts)
This challenge was on reverse engineering. The binary is 32bit MZ-PE executable for Windows. binary Summary: reverse engineering, crypto