Program is not packed x86 executable PE file.
binary
Dec 04
iCTF 2011. Challenge 30 ($500)
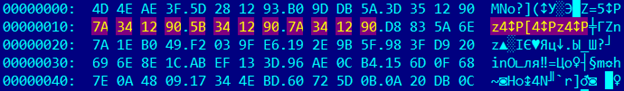
There is encrypted file “reverse2.7z.enc”. So if you look careful you see repeated pattern:
Dec 04
iCTF 2011. Challenge 31 ($ ?)
Program is not packed x86 executable ELF file.
There is a very easy logic here. Secret information about bank account is generated from input code.
Dec 04
iCTF 2011. Challenge 32 ($ ?)
Program is not packed x86 executable ELF file.
There is a very easy logic here. Secret information about bank account is generated from input code.
Dec 04
iCTF2011. Challenge 33 ($100)
There is file “reverse5”, but if you look at that, you don’t see executable file at all. It is some “binary trash”. Size is 991117 bytes and it looks like a packed one (large entropy).
Dec 03
The significant game, but EPIC FAIL! 2th on iCTF 2011
First of all, big thanks for UCSBiCTF ! It was really GREAT game!There are good task and services!
We played as More Smoked Leet Chicken (Leet More + Smoked Chicken) and It was the best game of those that I remember!
We have done a lot of tasks (most of all, if I’m not mistaken), had a lot of fun! But had some problem in trade :(
Oct 09
EnoWars CTF – GTFO (300 Pts)
Category: reverse, network
While trying to figure out how to leave, you notice some Rhynchodos millenios.
It’s really surprising to see one of those. Remember that documentary they had on Discovery Channel? They were pretty much the cheapest ships you could get. And they sucked. Big time. Being built with the cheapest materials around and constructed for less than minimum wage, they don’t always do what one might expect.
Enter your ship on timeslot.ivs.tu-berlin.de:10023, but beware: there might be some security around. If it takes you to long to get going, you might be caught. It’s not difficult to flee from them, but you will have to start all over again.
Perhaps the information you can find here (md5) will be helpful.
To see what you are doing go here .
Summary: reverse ELF for arm, analyze network communication command
Oct 08
EnoWars CTF – Get On Board (500)
Category: crypto
There is also this nice new spaceship in the hangar just waiting for us. Some old-school mobil terminal describes it as:
“The Heart of Gold is the sleekest, most advanced, coolest spaceship in the galaxy.
“Its stunning good looks mirror its awesome speed and power. It is powered by the revolutionary new Infinite Improbability Drive, which lets the ship pass through every point in every univese simultaneously.”
It looks a bit out of place in this death moon, but why should we not use it. After entering the ship (spaceship.ivs.tu-berlin.de:1337) you realize that it fails to start due to a simple bug in the code. But again you are lucky and find a printed copy of the source code of the signature verification system.
Oct 08
EnoWars CTF – Invaders 100 pts
Are you ready to fight?
Jedimaster: We can’t afford to wait any longer. Energy I’ll use to defeat their spaceships and clear the way for our troops.
Just me give a figher
Summary: packet analyze, a little reverse
Oct 02
rwth2011 CTF – mastermind
Mastermind was an easy service, written on Ruby.
Summary: SQL Injection, guessable id’s, guessable flag (by id)
Oct 01
rwth2011 CTF – ps3game
This service was on exploiting, understanding udp protocol and process of sign data.
ps3game files
Summary: reversing, crypto, rsa, tea hash, udp sign
Sep 30
Xakep Magazine. Defcon 19 CTF Report
Today October 10 (153) 2011 Xakep (“Hacker”) magazine issued with our (team IV) Defcon CTF report.
Sep 25
hack.lu CTF 2011 FluxScience (450)
Category: reversing
Thanks to a former employee of FluxScience (one of our competitors), we managed to get hands on some important files which might help us revealing company secrets. Attached you will find the files. The employee who provided them got fired. You might be lucky and find his account still working: FLUX-38B273DD75860083-0B3DD6B02EC5B9B1-4AFFBAC2EB8B4D17
He might not have the necessary permission to decrypt the personal data data.flux. he stole them from his boss, _GLaDOS_.
Would you mind helping us by finding their companysecret? download
Summary: reversing, VM, crypto, obfuscation, brainstorming
Sep 22
hack.lu CTF 2011 Wipe out the Klingons (400)
Category: crypto
We already made it. The evil Klingons agression is nearly fended. But their final mothership is well protected and even sacrifing a huge number of battleships caused only minor damage. Spies told us an unclear message caused most technical operators and the commander to leave the ship. Unfortunately we are unable to locate them. We need your help to decrypt the secret message in order to blow these little bastards up. Due to our attacks their RNG got damaged. Our mole reported us they use a manually chosen seed increased by one every time as a workaround.
nc ctf.hack.lu 2006
client.py
cryptor.py
ecc.py
capture.pcap
Summary: Elliptic curve Diffie-Hellman, several bugs in realization. 3 ways of solving