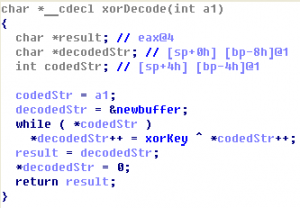
Let’s open this PE-file in IDA Pro. There is TLS-callback at address 0x00401450. TLS-callback is just anti-debugging trick (with SEH, dynamic import etc), so we can skip it and start execution from entry point: 0x00401000. On the entry point we can see some decoding cycle and one call at address 0x00401058. If we go into …
Category: Writeups
Mar 08
Codegate CTF 2011 Issue 500 (bootsector)
Find a key. [link to submit form] binary $ file challenge.bin challenge.bin: x86 boot sector, code offset 0xc0 Summary: bootsector with password check, bruteforcing 2 bytes hash.
Mar 08
Codegate CTF 2011 Crypto 400
The attacker got a secret! File Summary: Padding oracle attack analysis
Mar 07
Codegate CTF 2011 Forensic 300, Issue 300
Forensic 300 Description: We are investigating the military secret’s leaking.we found traffic with leaking secrets while monitoring the network.Security team was sent to investigate, immediately. But, there was no one present. It was found by forensics team that all the leaked secrets were completely deleted by wiping tool.And the team has found a leaked trace …
Mar 07
Codegate CTF 2011 Mini writeups
Some mini writeups on Codegate 2011 Prequals: Issue100,200, Net100,200, Crypto100,200.
Mar 07
Codegate CTF 2011 Crypto300 Writeup
Description: we are investigating an illegal online gambling site. To find any evidence to support for illegal gambling, we must access the oracle database with administrator privileges. The suspect says that he does not know the administrator password, but we know for sure that he is lying. The password is estimated to be longer than …
Jan 20
Padocon CTF 2011 Binary500 Writeup (300)
The challenge consists of a windows binary and connection details: HOST : 168.188.130.216 PORT : 888 Binary (Daemon.exe) Summary: reversing the algorithm with some encryption and coding a client
Jan 19
Padocon CTF 2011 Binary100 Writeup (200)
This task we were given a binary and a host/port where it is running: HOST : 168.188.130.217 PORT : 8080 Binary Note: At the beginning of the contest, there was no binary. But nobody solved it and the binary was added, I guess it’s because of strange format of the input. Summary: reversing (or guessing) …
Nov 02
Hack.lu 2010 CTF #22 (Pirates Wisdom) writeup
Pirates Wisdom Captian Iglo heard there is a secret wisdom in the well known pirate wisdom system. Log in to ssh pirates.fluxfingers.net:9022 user: ctf password: ctf and get the content of key.txt. You get rewarded with 300 coins. binary Summary: simple heap’s chunk reusage error with a bit obfuscated logic
Oct 31
Hack.lu 2010 CTF #1 (Fun 300, Rock Lizard Spock) writeup
On the high seas, the nights get boring. Try to win the game against the captain! pirates.fluxfingers.net port 6565/tcp Let’s go & connect there: > nc pirates.fluxfingers.net 6565 /9j/4AAQSkZJRgABAQEAYABgAAD//gAJbWQ1d2luc//bAEMABQ MEBAQDBQQEBAUFBQYHDAgHBwcHDwsLCQwRDxISEQ8RERMWHBcT <…> EgWAYlOhQqadCpxQPCn4JDjQoVacgqCQ4dtCAY4+FChVJb7BVE A6fCnKIB0+FChSuX3C8XQPuhoUKFd+JM//Z The service gives us some base64 and waits 2 seconds for reply. Unbase64ing the data, we get this jpeg: There is no …
Oct 31
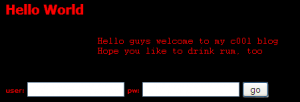
Hack.lu 2010 CTF #13 (My Cool Blog) writeup
Captain Rumbarrel is shocked because he found out that the filthy pirate Boozybold has stolen a whole shipment of rum! So Rumbarrel wants his revenge by hacking Boozybolds cool blog. Unfortunately he can not hack, so help him and get 250 gold coins! From main page of his cool blog, we get three main points: …
Oct 31
Hack.lu 2010 CTF #3, #11, #14 (Most Epic Challenges :) writeup
Task #3 – Like skies that are so blue Sometime even pirates have a lazy sunday… download 0. 1. Open in your favorite image editor (ms paint) 2. Do a fill: 3. Md5 of the original file is the answer: 032c49411912397eea2a7d906dab5f7e Task #11 – Ecrime Business Cap’n Bill Greasepalms wants to start an ecrime business. …
Oct 31
Hack.lu 2010 CTF #17 (Brainfuck) writeup
You found a backdoor on Captain Brainfuck’s webspace. Exploit it and read his secret file! The page only says ‘happy hacking’, so what would we be doing without its source… [source mirror] “Source” in fact is a zip archive with php code appended: PK <..zip binary trash..> <?php @ob_clean();$z=zip_open(__FILE__); eval($f=zip_entry_read(zip_read($z),1000));@ob_end_flush();?> It simply reads itself (the …
Oct 31
Hack.lu 2010 CTF #16 (Rattlesnake’s Riddle) writeup
Solve this riddle to impress Captain Rattlesnake! download The .pyc file is a byte-compiled python code, and there is a wonderful tool called uncompyle to deal with it. $ decompyle secret.pyc > secret.py The decompyled file: 1. Takes 3 arguments 2. Checks 2nd to be 1337 3. Calculates ‘token‘ value, which is 11111112671 4. After some …
Oct 30
Hack.lu 2010 CTF Challenge #8 Writeup
Sad Little Pirate (150) Our sad little pirate haes lost his password. It is known that the pirate has just one hand left; his left hand. So the paessword input is quite limited. Also he can still remember that the plaintext started with “674e2” and his password with “wcwteseawx” Please help the sad pirate finding …