□ description ========================================== ssh guest@58.229.183.14 / ExtremelyDangerousGuest ssh guest@58.229.183.15 / ExtremelyDangerousGuest ========================================== □ number of solvers : 15 □ breakthrough by 1 : More Smoked Leet Chicken (02/23 02:38) 2 : Hexcellents (02/23 02:42) 3 : ppp (02/23 03:16) Binary
Category: Writeups
Feb 09
Olympic CTF 2014 GuessGame (300)
Be careful, it’s cheating! nc 109.233.61.11 3126 Summary: discrete logarithm with group oracle
Oct 25
Hack.lu 2013 CTF – Crypto 350 (BREW’r’Y)
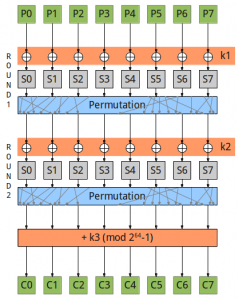
BREW’r’Y (Category: Crypto) Author(s): dwuid Finally, the robots managed to sneak into one of our breweries. I guess I won’t have to explain how bad that really is. That darn non-physical ones even shutdown our login system. Shiny thing, advanced technology, all based on fingerprints. Been secure as hell. If only it was running. Well, …
Jun 17
Defcon CTF Quals 2013 – \xff\xe4\xcc 4 (penser)
good luck. penser.shallweplayaga.me:8273 http://assets-2013.legitbs.net/liabilities/penser Download penser binary » Summary: x86_64 Unicode-proof shellcoding.
Jun 17
Defcon CTF Quals 2013 – \xff\xe4\xcc 3 (linked)
typedef struct _llist { struct _llist *next; uint32_t tag; char data[100]; llist; and: register char *answer; char *(*func)(); llist *head; … func = (char *(*)(llist *))userBuf; answer = (char *)(*func)(head); send_string(answer); exit(0); Write me shellcode that traverses the randomly generated linked list, looking for a node with a tag 0x41414100, and returns a pointer to …
Jun 17
Defcon CTF Quals 2013 – All Web Challenges (3dub)
Summary: 3dub (1) – babysfirst: SQLite SQL injection 3dub (2) – badmedicine: Stream cipher bit flipping 3dub (3) – hypeman: Rack/Sinatra session secret disclosure 3dub (4) – rememberme: Bruteforce 3dub (5) – worsemedicine: Block cipher bit flipping
Jun 02
PHD CTF 2013 Hackskell (500)
We’ve got a screenshot of some encryption, here’s the text transcribed. Please say what’s there. Summary: a couple of modular equations
Jun 02
PHD CTF 2013 from hell import crypto (100)
Decrypt the message: 7y9rr177sluqv1r4pw Hint: $ at
Jun 02
PHD CTF 2013 ReStART (400)
We heard hellman encrypted the flag using his super secure keygen. Break it! Summary: RSA with the lower half of the secret exponent bits leaked.
Apr 22
PlaidCTF 2013 Blech (Crypto 200)
You get arbitrary code execution…. as long as it’s code we approve of. Source available at blech.py Service running on 54.234.73.81 port 1234 blech.py Summary: RSA cube root attack
Nov 19
PoliCTF 2012 pwn/bin 200
Play with this amazing calculator: calc.challenges.polictf.it:4000 Summary: Scheme eval
Nov 19
PoliCTF 2012 Crypto 500
Hensel and Gretel are looking for their new house, but the twisted seller who sold it to them decided to provide the coordinates to their new love nest only after ensuring that the couple is Smart enough to earn them. Thus, the seller provides them with the following map and leaves Hensel and Gretel to …
Nov 19