Program is not packed x86 executable PE file. binary
Tag: reverse
Dec 04
iCTF 2011. Challenge 30 ($500)
There is encrypted file “reverse2.7z.enc”. So if you look careful you see repeated pattern:
Dec 04
iCTF 2011. Challenge 31 ($ ?)
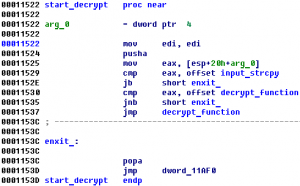
Program is not packed x86 executable ELF file. There is a very easy logic here. Secret information about bank account is generated from input code.
Dec 04
iCTF 2011. Challenge 32 ($ ?)
Program is not packed x86 executable ELF file. There is a very easy logic here. Secret information about bank account is generated from input code.
Oct 01
rwth2011 CTF – ps3game
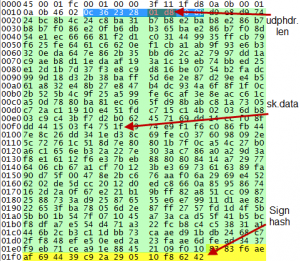
This service was on exploiting, understanding udp protocol and process of sign data. ps3game files Summary: reversing, crypto, rsa, tea hash, udp sign
Sep 21
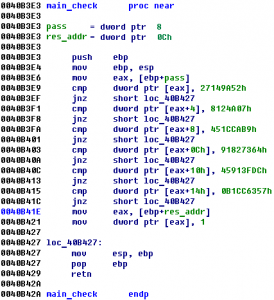
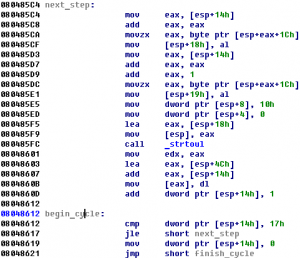
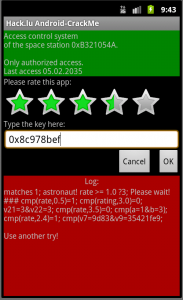
hack.lu CTF 2011 Space Station 0xB321054A (300)
Category: exploiting You have seen a deserted space station. Your task is to enter it. The first barrier is the access system. But you can find a module with the application on it. Here is the file: download What is the key? (There is also station A, but station B is the advanced one.) Summary: …
Jul 25
NdH2k11 WaRgam3 – CrackMe 400 (2000pts). Part 2
It is second part of CrackMe task describing. First one you can find there In this part I will detail the analysis of driver ReverMe1.sys
Jun 06
Defcon CTF Quals 2011 – Pwnables 400
This challenge was on remote exploiting. The binary is for Linux, statically linked and stripped. binary Summary: overflow, ROP for execve(“/bin/sh”)
Mar 09
Codegate CTF 2011 Vuln 300
This challenge was an exploitation of suid binary. binary Summary: ROPing buffer overflow with NX and ASLR
Mar 08
Codegate CTF 2011 Issue 500 (bootsector)
Find a key. [link to submit form] binary $ file challenge.bin challenge.bin: x86 boot sector, code offset 0xc0 Summary: bootsector with password check, bruteforcing 2 bytes hash.
Jan 20
Padocon CTF 2011 Binary500 Writeup (300)
The challenge consists of a windows binary and connection details: HOST : 168.188.130.216 PORT : 888 Binary (Daemon.exe) Summary: reversing the algorithm with some encryption and coding a client
Jan 19
Padocon CTF 2011 Binary100 Writeup (200)
This task we were given a binary and a host/port where it is running: HOST : 168.188.130.217 PORT : 8080 Binary Note: At the beginning of the contest, there was no binary. But nobody solved it and the binary was added, I guess it’s because of strange format of the input. Summary: reversing (or guessing) …
Oct 31
Hack.lu 2010 CTF #3, #11, #14 (Most Epic Challenges :) writeup
Task #3 – Like skies that are so blue Sometime even pirates have a lazy sunday… download 0. 1. Open in your favorite image editor (ms paint) 2. Do a fill: 3. Md5 of the original file is the answer: 032c49411912397eea2a7d906dab5f7e Task #11 – Ecrime Business Cap’n Bill Greasepalms wants to start an ecrime business. …
Sep 21
Leet More 2010 Jailbreak writeup
Category: CTB A piece of code is currently up @ ctf.ifmo.ru:4004 BTW, here is what’s inside the jail: vos@ms7:~/private_data$ ls -la total 20K d——r-x 2 alice alice 4.0K Aug 21 00:23 . d——r-x 3 alice alice 4.0K Aug 21 00:29 .. ——-r– 1 alice alice 9.0K Aug 21 00:23 key Ok, we have this binary …
Sep 21
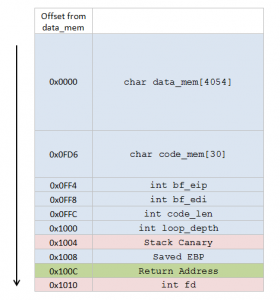
Leet More 2010 brainfffuuuuu writeup
Category: CTB This binary is running at ctf.ifmo.ru Are you able to get the key?! Let’s take a look at what the binary is doing (decompilation of its main function begin_the_fucking() will help us): 1. Prints out some prompt 2. Reads 30 bytes 3. Interprets them as Brainfuck code. and here is what the stack …