Task #3 – Like skies that are so blue
Sometime even pirates have a lazy sunday…
download
0. 
1. Open in your favorite image editor (ms paint)
2. Do a fill: 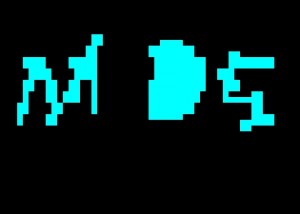
3. Md5 of the original file is the answer: 032c49411912397eea2a7d906dab5f7e
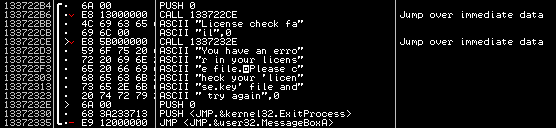
Task #11 – Ecrime Business
Cap’n Bill Greasepalms wants to start an ecrime business.
If you want to join his crew you have to proof your pdf skillz.
Get the secret key and you get 100 coins.
download
This one has two character encodings inside:
1. #XX means chr(0xXX)
2. \ooo means chr(octdec(ooo))
Also, it has extra “\\\r\n” sequences for obfuscation.
Script for stripping the obfuscation:
<?php $f = file_get_contents("ecrime.pdf"); $f = preg_replace('/#([a-f0-9]{2})/sie', 'chr(hexdec("$1"))', $f); $f = preg_replace('#\\\\(\d{3})#sie', 'chr(octdec("$1"))', $f); $f = str_replace("\\\r\n", '', $f); file_put_contents("ecrime.out.pdf", $f); ?>
Inside ecrime.out.pdf, a javascript is easily noticed. Replace eval with alert and execute in a browser: [ecrime_js.htm]
Answer: 45cd5f86ea1b489e4a5e86b98
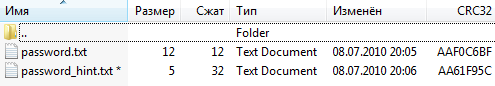
Task #14 – Captain Flints Key
Little Bobby Flint was able to download a file containing the key for Captian Flints treasure chest.
Unfortunately the download finished incorrectly and the file is corrupt.
Help him to recover the key and gain 200 gold coins.
download
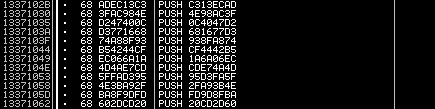
1. Rebuild the zip archive using WinRAR: [rebuilt.dump.zip]
2. Extract org.exe (crc won’t match)
3. Rebuild orig.exe using PETools: [org_rebuilt.exe]
> org_rebuilt.exe The Key is: 183808af