Category: pwnables They have an update for the vulnerable C++ program trying to fix the bug. However, the coders at AED suck and introduced another stupid mistake. Get a shell (and the key, too.) ssh username@a5.amalgamated.biz Username: cpp2_1 Password: zKQaKrdFPSsT6j03XSt31NaT0H Summary: tricky overflow class’ method and exec’ing symlinks binary
Tag: ctf
Apr 09
Nuit du hack 2011 CTF Forensic
Forensic 100 On a dumpe la RAM d’une machine sur laquelle tournait un serveur VNC. Le but est de recupere le mot de passe de ce serveur. * * * We have dumped the RAM of a Machine on which was running a VNC server. The goal is to get the password of that VNC …
Mar 07
Codegate CTF 2011 Forensic 300, Issue 300
Forensic 300 Description: We are investigating the military secret’s leaking.we found traffic with leaking secrets while monitoring the network.Security team was sent to investigate, immediately. But, there was no one present. It was found by forensics team that all the leaked secrets were completely deleted by wiping tool.And the team has found a leaked trace …
Jan 20
Padocon CTF 2011 Binary500 Writeup (300)
The challenge consists of a windows binary and connection details: HOST : 168.188.130.216 PORT : 888 Binary (Daemon.exe) Summary: reversing the algorithm with some encryption and coding a client
Jan 19
Padocon CTF 2011 Binary100 Writeup (200)
This task we were given a binary and a host/port where it is running: HOST : 168.188.130.217 PORT : 8080 Binary Note: At the beginning of the contest, there was no binary. But nobody solved it and the binary was added, I guess it’s because of strange format of the input. Summary: reversing (or guessing) …
Oct 31
Hack.lu 2010 CTF #1 (Fun 300, Rock Lizard Spock) writeup
On the high seas, the nights get boring. Try to win the game against the captain! pirates.fluxfingers.net port 6565/tcp Let’s go & connect there: > nc pirates.fluxfingers.net 6565 /9j/4AAQSkZJRgABAQEAYABgAAD//gAJbWQ1d2luc//bAEMABQ MEBAQDBQQEBAUFBQYHDAgHBwcHDwsLCQwRDxISEQ8RERMWHBcT <…> EgWAYlOhQqadCpxQPCn4JDjQoVacgqCQ4dtCAY4+FChVJb7BVE A6fCnKIB0+FChSuX3C8XQPuhoUKFd+JM//Z The service gives us some base64 and waits 2 seconds for reply. Unbase64ing the data, we get this jpeg: There is no …
Oct 31
Hack.lu 2010 CTF #13 (My Cool Blog) writeup
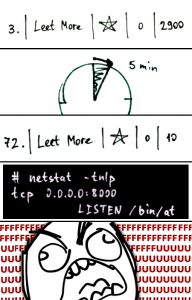
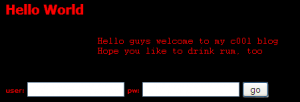
Captain Rumbarrel is shocked because he found out that the filthy pirate Boozybold has stolen a whole shipment of rum! So Rumbarrel wants his revenge by hacking Boozybolds cool blog. Unfortunately he can not hack, so help him and get 250 gold coins! From main page of his cool blog, we get three main points: …
Oct 31
Hack.lu 2010 CTF #3, #11, #14 (Most Epic Challenges :) writeup
Task #3 – Like skies that are so blue Sometime even pirates have a lazy sunday… download 0. 1. Open in your favorite image editor (ms paint) 2. Do a fill: 3. Md5 of the original file is the answer: 032c49411912397eea2a7d906dab5f7e Task #11 – Ecrime Business Cap’n Bill Greasepalms wants to start an ecrime business. …
Oct 31
Hack.lu 2010 CTF #17 (Brainfuck) writeup
You found a backdoor on Captain Brainfuck’s webspace. Exploit it and read his secret file! The page only says ‘happy hacking’, so what would we be doing without its source… [source mirror] “Source” in fact is a zip archive with php code appended: PK <..zip binary trash..> <?php @ob_clean();$z=zip_open(__FILE__); eval($f=zip_entry_read(zip_read($z),1000));@ob_end_flush();?> It simply reads itself (the …
Oct 31
Hack.lu 2010 CTF #16 (Rattlesnake’s Riddle) writeup
Solve this riddle to impress Captain Rattlesnake! download The .pyc file is a byte-compiled python code, and there is a wonderful tool called uncompyle to deal with it. $ decompyle secret.pyc > secret.py The decompyled file: 1. Takes 3 arguments 2. Checks 2nd to be 1337 3. Calculates ‘token‘ value, which is 11111112671 4. After some …
Oct 30
Hack.lu 2010 CTF Challenge #8 Writeup
Sad Little Pirate (150) Our sad little pirate haes lost his password. It is known that the pirate has just one hand left; his left hand. So the paessword input is quite limited. Also he can still remember that the plaintext started with “674e2” and his password with “wcwteseawx” Please help the sad pirate finding …
Oct 30
Hack.lu 2010 CTF Challenge #7 Writeup
Breiers Deathmatch (150) Schnuce Breier has challenged you to a cryptographer’s deathmatch. Connect to pirates.fluxfingers.net 8007/tcp and get the secret number. $ nc pirates.fluxfingers.net 8007 Hi. This is your friendly ‘Decryption Oracle’ We have implemented a well-known public-key cryptosystem. Guess which ;) Modulo: 5628290459057877291809182450381238927697314822133923421169378 062922140081498734424133112032854812341 Generator: 99 Public Key: 135744434201778324839308712462911647727754874814096844915 5264250239122362719894347099351280643528244 Ciphertext: (44750535504622985677351849167148532593337860047243938284 03819968944371696234280482660523326406427034, 40867215175893797288404 …
Oct 30
Hack.lu 2010 CTF Challenge #10 Writeup
#10 – Chip Forensic To solve this task we have something like this (original image is lost) and hex string: 0B 12 0F 0F 1C 4A 4C 0D 4D 15 12 0A 08 15. What we see on image? Some USB device. Those who have seen them on ebay or on other sites knows that …
Oct 30
Hack.lu 2010 CTF Challenge #5 Writeup
Captain Redbeard’s Battleships (500) While pirating-out a bit, you run into Captain Redbeard and his armada of ghost ships. source1, source2 pirates.fluxfingers.net 2204 /tcp. It is a Battleships game. We have to win Cpt. Redbeard 3 times in a row, to get the flag. First time he shots every 3 ships from 5, than 4 …