Because of vulnerability of site in Company A, database which contains user’s information was leaked. The file is dumped packet at the moment of attacking. Find the administrator’s account information which was leaked from the site. For reference, some parts of the packet was blind to XXXX. Answer : strupr(md5(database_name|table_name|decode(password_of_admin))) (‘|’is just a character) Download …
Tag: 2012
Feb 26
CodeGate 2012 Quals – Vuln 300
Here we are given ssh credentials where we need to exploit the binary. Summary: compose file to make program jump to stack.
Feb 26
CodeGate 2012 Quals – Vuln 200
This web challenge is again about uploading. Our aim was to get shell. Summary: upload php shell, read the key.
Feb 26
CodeGate 2012 Quals – Vuln 100
This challenge is a web service where one can upload mp3 files and listen to them. Our aim is to get admin’s song. Summary: sql injection
Feb 26
CodeGate 2012 Quals – Binary 200
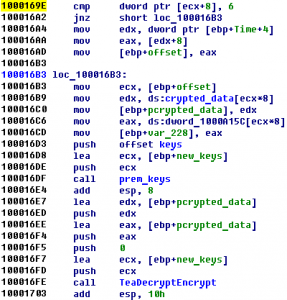
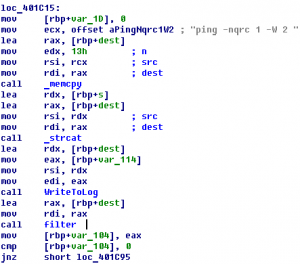
Find a printable string that the program would print ultimately. Down (pw: infected) Summary: unpack, XTEA decrypt
Feb 13
IFSF CTF #7 (X99) Write-up
this is one of their machines which have very sensitive informations , try to get for us the password 208.64.122.27 PORT : 3000 X99 carries a synthetic vulnerability that allows a char-by-char password bruteforce.
Feb 13
IFSF CTF Small Challenges (#4, #5, #6, #14, #15)
Contents #4 ER #5 Change #6 Call me #14 Seek me #15 Embedded docs
Feb 13
IFSF CTF 2012 #9 – X97
SSH : 208.64.122.235 guest:guest binary Category: exploitation Summary: format string bug, ASLR and NX
Feb 05
Gits 2012 #13
File was running at kimjongun.final2012.ghostintheshellcode.com : 2645 Summary: buffer overflow, reverse
Feb 05
Gits 2012 #12
File was running at gratis.final2012.ghostintheshellcode.com:3030 Summary: reverse, x64, filtering parameters error
Jan 30
Gits 2012 # – Crypto 400
files running at hellothere.final2012.ghostintheshellcode.com Summary: MITM attack
Jan 30
Gits 2012 #14 Pwnable (300)
Jacked file running at jacked.final2012.ghostintheshellcode.com:2121 Summary: weak random, BlackJack bot, format string
Jan 30
Gits 2012 #7 – Reversing (300)
Question: Fanatic 300 Points Remeber the past. (Link) Here we have a NES emulator written on javascript. ROM can easily be dumped from there.
Jan 30
Gits 2012 #5 – Forensics (400)
Question: VoxVeritas 400 Points Find the secret passage. (File)