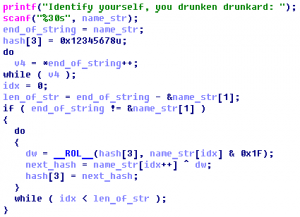
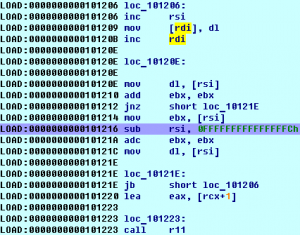
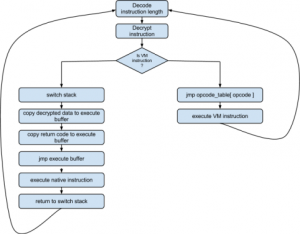
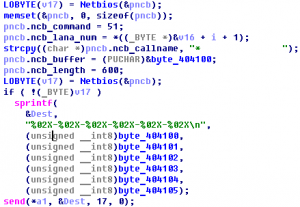
Talent Yang loves to customize his own obfuscator. Unfortunately, he lost his seed when he was watching Arsenal’s UEFA game. What a sad day! His team and his seed were lost together. To save him, could you help him to get back his seed? We can not save the game, but we may be able …
Tag: reverse
Oct 11
HITCON CTF QUALS 2016 – Reverse (Reverse + PPC 500)
At least our ETA is better than M$. http://xkcd.com/612/ reverse.bin Summary: optimizing an algorithm using Treap data structure and CRC32 properties.
Feb 02
Olympic CTF Sochi 2014 Registration is Open
Let there be Olympics MSLC proudly presents…Alright, do we even need words here? Game starts: February 7th, 2014 16:14 UTC (yeah yeah, those Sochi number freaks… it’s 20:14 in MSK timezone) Game ends: February 9th, 2014 16:14 UTC Sign up: https://olympic-ctf.ru/ Prize set: 1500 USD, 1000 USD, 500 USD. Expect decent tasks. Twenty of them.
Jan 07
Sudden CTF syndrome
Happy new 2014 and merry Orthodox Christmas if you’re religious ;-D Maybe you already know hack you and hack you too, so I won’t even say that hack you is an individual CTF that we originally held for our university freshmen and opened it for everyone interested in the world. Couple days after this New …
Nov 04
Hack.lu 2012 CTF Challenge #12 (500)
The famous zombie researcher “Donn Beach” almost created an immunization against the dipsomanie virus. This severe disease leads to the inability to defend against Zombies, later causes a complete loss of memory and finally turns you into one of them. Inexplicably Donn forgot where he put the license key for his centrifuge. Provide him a …
May 01
SIMD [250] (Pirating)
After examining some code retrieved by our operative we are unsure whether it was written by an evil genius or a google employee. We will let you decide. Summary: linux x64 binary, obfuscated xor
Apr 30
PlaidCTF 2012 – Bouncer [250] (Practical Packets)
In a recent battle we took an enemy robot hostage and examined his operating system. During the examination we found a piece of robot malware that we don’t quite understand. Can you enumerate its targets? This challenge was made by our friends at ManTech. If you enjoyed it, you might be interested in working for them. Summary: unpack …
Feb 27
CodeGate 2012 Quals – Binary 300
There are malicious program associated with DDoS zombie. Calcurate the sum of port numbers used for the attack. And, how many times does zombie try to attack? Answer: sum(attack_ports) * attack_count (* : multiplication) Download : 72C4DAA981E17282B12E6226A1D60162 Summary: unpack, malware analyse
Feb 26
CodeGate 2012 Quals – Vuln 300
Here we are given ssh credentials where we need to exploit the binary. Summary: compose file to make program jump to stack.
Feb 26
CodeGate 2012 Quals – Binary 200
Find a printable string that the program would print ultimately. Down (pw: infected) Summary: unpack, XTEA decrypt
Feb 13
IFSF CTF 2012 #9 – X97
SSH : 208.64.122.235 guest:guest binary Category: exploitation Summary: format string bug, ASLR and NX
Feb 05
Gits 2012 #13
File was running at kimjongun.final2012.ghostintheshellcode.com : 2645 Summary: buffer overflow, reverse
Feb 05
Gits 2012 #12
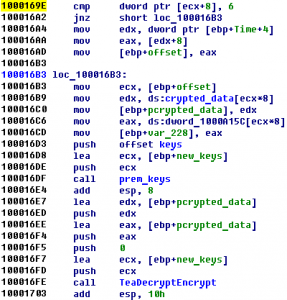
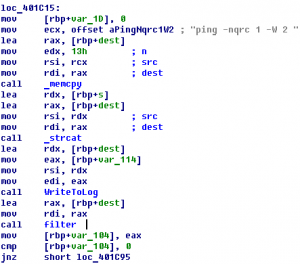
File was running at gratis.final2012.ghostintheshellcode.com:3030 Summary: reverse, x64, filtering parameters error
Jan 27
MozillaCTF 2012 AwesomeCorp. Secured Ranges (300) Writeup
One evening, you decide to take a look at the website of Awesome Corp., a competitor which you suspect of reverse-engineering parts of your software and using these code pieces in their own product. Unfortunately, you got no proof, so you begin to investigate on your own. Soon enough (insert random webhacking stuff here), you …