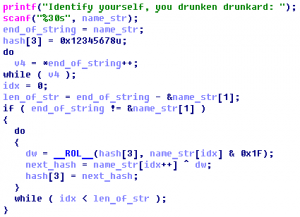
The famous zombie researcher “Donn Beach” almost created an immunization against the dipsomanie virus. This severe disease leads to the inability to defend against Zombies, later causes a complete loss of memory and finally turns you into one of them. Inexplicably Donn forgot where he put the license key for his centrifuge. Provide him a …
Tag: vm
Mar 26
NuitDuHack 2012 Prequals – Web3.ndh
Our spy thinks that Sciteek staff is aware about the mole inside their building. He is trying to read a private file named “sciteek-private.txt” located at sciteek.nuitduhack.com:4005. Please find the .ndh attached, if you are sucessfull, reply with a message entitled “complex remote service”. Of course, your efforts will be rewarded with $2500. Maybe you …
Mar 26
NuitDuHack 2012 Prequals – executable1.ndh
Meanwhile, we got fresh news from our mystery guy. He came along with an intersting binary file. It just looks like an executable, but it is not ELF nor anything our experts would happen to know or recognize. Some of them we quite impressed by your skills and do think you may be able to …
Mar 26
NuitDuHack 2012 Prequals – executable2.ndh
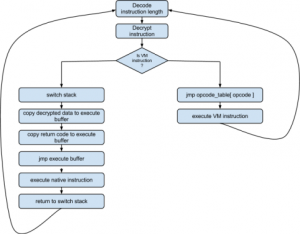
Our anonymous guy managed to get access to another bunch of files. We also need to get as much information as possible about the file itself. If you succeed, you will be rewarded with $2500 for the ndh file. executable2.ndh NDH Virtual Machine Summary: VM in the NDH VM, crackme
Jun 09
Defcon CTF Quals 2011 – Retro 400
This challenge was on remote exploiting. The binary is for FreeBSD. The program is some kind of a Virtual Machine, with it’s own stack and memory. binary Summary: memory address check mistake, write shellcode and overwrite _exit function pointer
Sep 14
Leet More 2010 Stack or what? writeup
We received a new CPU model, you are to make a vulnerability check. Enter the CPU secret code as a proof. [ ctf.ifmo.ru:3123 ] + binary Here we have a VM with a few instuctions: nop, add, xor, mul, push, pop, loop, pops, pushs and core. The most intresting is core – it spawns a …