This challenge was an exploitation of suid binary. binary Summary: ROPing buffer overflow with NX and ASLR
March 2011 archive
Mar 08
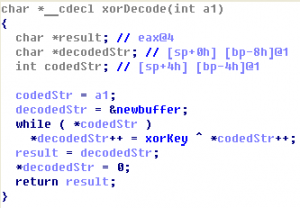
Codegate CTF 2011 Binary 200
Let’s open this PE-file in IDA Pro. There is TLS-callback at address 0x00401450. TLS-callback is just anti-debugging trick (with SEH, dynamic import etc), so we can skip it and start execution from entry point: 0x00401000. On the entry point we can see some decoding cycle and one call at address 0x00401058. If we go into …
Mar 08
Codegate CTF 2011 Issue 500 (bootsector)
Find a key. [link to submit form] binary $ file challenge.bin challenge.bin: x86 boot sector, code offset 0xc0 Summary: bootsector with password check, bruteforcing 2 bytes hash.
Mar 08
Codegate CTF 2011 Crypto 400
The attacker got a secret! File Summary: Padding oracle attack analysis
Mar 07
Codegate CTF 2011 Forensic 300, Issue 300
Forensic 300 Description: We are investigating the military secret’s leaking.we found traffic with leaking secrets while monitoring the network.Security team was sent to investigate, immediately. But, there was no one present. It was found by forensics team that all the leaked secrets were completely deleted by wiping tool.And the team has found a leaked trace …
Mar 07
Codegate CTF 2011 Mini writeups
Some mini writeups on Codegate 2011 Prequals: Issue100,200, Net100,200, Crypto100,200.
Mar 07
Codegate CTF 2011 Crypto300 Writeup
Description: we are investigating an illegal online gambling site. To find any evidence to support for illegal gambling, we must access the oracle database with administrator privileges. The suspect says that he does not know the administrator password, but we know for sure that he is lying. The password is estimated to be longer than …