vos and snk from MSLC share their basic view of Attack-Defence CTFs and tell random stories in their two-hour talk at Chaos Constructions 2014. With English subtitles
Tag: defcon
Jun 17
Defcon CTF Quals 2013 – \xff\xe4\xcc 4 (penser)
good luck. penser.shallweplayaga.me:8273 http://assets-2013.legitbs.net/liabilities/penser Download penser binary » Summary: x86_64 Unicode-proof shellcoding.
Jun 17
Defcon CTF Quals 2013 – \xff\xe4\xcc 3 (linked)
typedef struct _llist { struct _llist *next; uint32_t tag; char data[100]; llist; and: register char *answer; char *(*func)(); llist *head; … func = (char *(*)(llist *))userBuf; answer = (char *)(*func)(head); send_string(answer); exit(0); Write me shellcode that traverses the randomly generated linked list, looking for a node with a tag 0x41414100, and returns a pointer to …
Jun 17
Defcon CTF Quals 2013 – All Web Challenges (3dub)
Summary: 3dub (1) – babysfirst: SQLite SQL injection 3dub (2) – badmedicine: Stream cipher bit flipping 3dub (3) – hypeman: Rack/Sinatra session secret disclosure 3dub (4) – rememberme: Bruteforce 3dub (5) – worsemedicine: Block cipher bit flipping
Sep 13
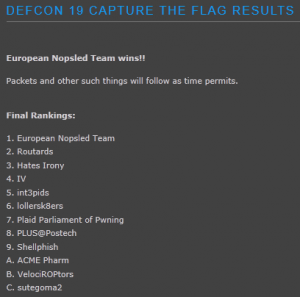
DEFCON 19 Final – hiver
This challenge was on logic and understanding of the bloom filter. The binary is for FreeBSD. binary Summary: understanding of the bloom filter, bruteforce bloom filter set.
Sep 13
DEFCON 19 Final – forgetu
This challenge was on remote exploiting. The binary is for FreeBSD. binary Summary: bruteforce password, buffer overflow, jump to shellcode
Jun 09
Defcon CTF Quals 2011 – Retro 400
This challenge was on remote exploiting. The binary is for FreeBSD. The program is some kind of a Virtual Machine, with it’s own stack and memory. binary Summary: memory address check mistake, write shellcode and overwrite _exit function pointer
Jun 08
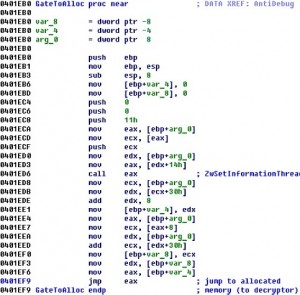
Defcon CTF Quals 2011 – Binary 500
This challenge was on reverse engineering. The binary is 32bit MZ-PE executable for Windows. binary Summary: reverse engineering, anti-anti-debugging challenge
Jun 07
Defcon CTF Quals 2011 – Pwnables 100
This challenge was on remote exploiting. The binary is for FreeBSD. binary Summary: buffer overflow, jump to shellcode (bruteforce address)
- 1
- 2