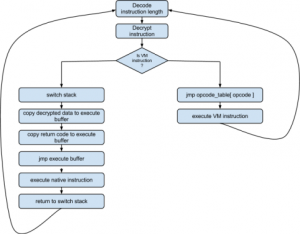
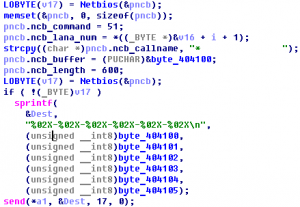
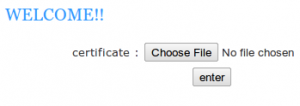
Seeing that it is not all. Down Summary: VM analysis, python decompiling
February 2012 archive
Feb 27
CodeGate 2012 Quals – Binary 300
There are malicious program associated with DDoS zombie. Calcurate the sum of port numbers used for the attack. And, how many times does zombie try to attack? Answer: sum(attack_ports) * attack_count (* : multiplication) Download : 72C4DAA981E17282B12E6226A1D60162 Summary: unpack, malware analyse
Feb 26
CodeGate 2012 Quals Forensic 500 Write-up
This file is Forensic file format which is generally used. Check the information of imaged DISK, find the GUIDs of every partition. Answer: strupr((part1_GUID) XOR (part2_GUID) XOR …) Download : B704361ACF90390C17F6103DF4811E2D Forensic 500 features EWF format container with EFI GPT partition table.
Feb 26
CodeGate 2012 Quals Vuln500 Write-up
1.234.41.7:22 ID : yesMan PWD : ohyeah123 Download vulnerable binary. Vuln500 was a hardened format-string vuln with ASLR, NX-stack, no-DTORs, RO .dynamic
Feb 26
CodeGate 2012 Quals Net400 Write-up
Because of vulnerability of site in Company A, database which contains user’s information was leaked. The file is dumped packet at the moment of attacking. Find the administrator’s account information which was leaked from the site. For reference, some parts of the packet was blind to XXXX. Answer : strupr(md5(database_name|table_name|decode(password_of_admin))) (‘|’is just a character) Download …
Feb 26
CodeGate 2012 Quals – Vuln 300
Here we are given ssh credentials where we need to exploit the binary. Summary: compose file to make program jump to stack.
Feb 26
CodeGate 2012 Quals – Vuln 200
This web challenge is again about uploading. Our aim was to get shell. Summary: upload php shell, read the key.
Feb 26
CodeGate 2012 Quals – Vuln 100
This challenge is a web service where one can upload mp3 files and listen to them. Our aim is to get admin’s song. Summary: sql injection
Feb 26
CodeGate 2012 Quals – Binary 200
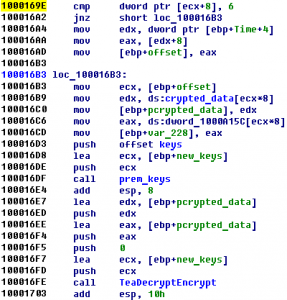
Find a printable string that the program would print ultimately. Down (pw: infected) Summary: unpack, XTEA decrypt
Feb 13
IFSF CTF #7 (X99) Write-up
this is one of their machines which have very sensitive informations , try to get for us the password 208.64.122.27 PORT : 3000 X99 carries a synthetic vulnerability that allows a char-by-char password bruteforce.
Feb 13
IFSF CTF Small Challenges (#4, #5, #6, #14, #15)
Contents #4 ER #5 Change #6 Call me #14 Seek me #15 Embedded docs
Feb 13
IFSF CTF 2012 #9 – X97
SSH : 208.64.122.235 guest:guest binary Category: exploitation Summary: format string bug, ASLR and NX
- 1
- 2