□ description ========================================== OS : Ubuntu 13.10 x86 IP : 58.229.183.18 / TCP 8888 http://58.229.183.26/files/angry_doraemon_c927b1681064f78612ce78f6b93c14d9 ========================================== □ number of solvers : 57 □ breakthrough by 1 : More Smoked Leet Chicken (02/23 06:16) 2 : ppp (02/23 06:22) 3 : stratumauhuur (02/23 06:28) Binary
Tag: exploitation
Feb 24
Codegate 2014 Quals – Minibomb (pwn 400)
□ description ========================================== ssh guest@58.229.183.14 / ExtremelyDangerousGuest ssh guest@58.229.183.15 / ExtremelyDangerousGuest ========================================== □ number of solvers : 15 □ breakthrough by 1 : More Smoked Leet Chicken (02/23 02:38) 2 : Hexcellents (02/23 02:42) 3 : ppp (02/23 03:16) Binary
May 01
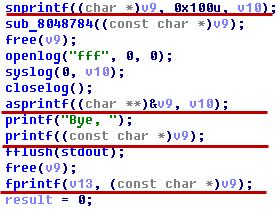
PlaidCTF 2012 – Format [99] (Pwnables)
Up on a hill, far away, sits the robot king of old. While he was once great, he recently has seemed to just offer simple challenges. Vanquish him and bring honor to your team! Summary: rand guessing, format string exploitation
Feb 26
CodeGate 2012 Quals – Vuln 300
Here we are given ssh credentials where we need to exploit the binary. Summary: compose file to make program jump to stack.