Heading up the steeple gave you and your companion a nice view over the outbreak situation in your city. But it also attracted a lot of unwanted attention. Zombies are surrounding your spot and are looking for an entrance to the building. You obviously need some bait to lure them away so you can flee …
Tag: reversing
Oct 04
Announcing hackyou CTF
It’s fall already and that means the new CTF season is starting, and so is the new academic year in our university. This is the time when we want to attract more freshmen into our CTF tarpit ;-D So we are running – a CTF. But it’s not just for them. Wouldn’t it be fun …
Dec 04
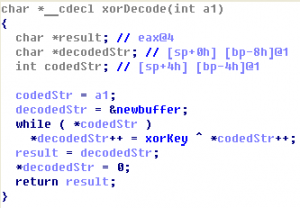
iCTF 2011. Challenge 31 ($ ?)
Program is not packed x86 executable ELF file. There is a very easy logic here. Secret information about bank account is generated from input code.
Sep 25
hack.lu CTF 2011 FluxScience (450)
Category: reversing Thanks to a former employee of FluxScience (one of our competitors), we managed to get hands on some important files which might help us revealing company secrets. Attached you will find the files. The employee who provided them got fired. You might be lucky and find his account still working: FLUX-38B273DD75860083-0B3DD6B02EC5B9B1-4AFFBAC2EB8B4D17 He might …
Mar 08
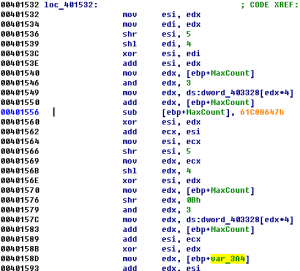
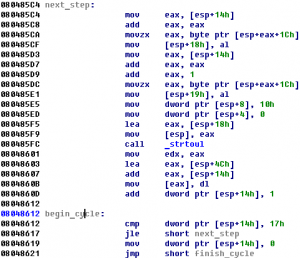
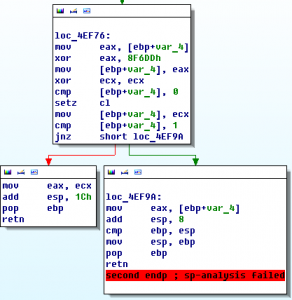
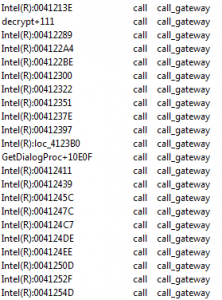
Codegate CTF 2011 Binary 200
Let’s open this PE-file in IDA Pro. There is TLS-callback at address 0x00401450. TLS-callback is just anti-debugging trick (with SEH, dynamic import etc), so we can skip it and start execution from entry point: 0x00401000. On the entry point we can see some decoding cycle and one call at address 0x00401058. If we go into …
Nov 02
Hack.lu 2010 CTF #22 (Pirates Wisdom) writeup
Pirates Wisdom Captian Iglo heard there is a secret wisdom in the well known pirate wisdom system. Log in to ssh pirates.fluxfingers.net:9022 user: ctf password: ctf and get the content of key.txt. You get rewarded with 300 coins. binary Summary: simple heap’s chunk reusage error with a bit obfuscated logic