Let’s open this PE-file in IDA Pro. There is TLS-callback at address 0x00401450. TLS-callback is just anti-debugging trick (with SEH, dynamic import etc), so we can skip it and start execution from entry point: 0x00401000.
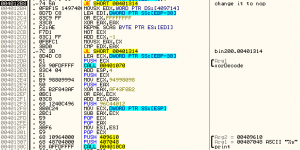
On the entry point we can see some decoding cycle and one call at address 0x00401058. If we go into call, we can see two interesting calls at the end of procedure (0x004012DB: CALL 00401070 and 0x0040130C: CALL 004010C0). But we can’t jump on that calls because JE operation at address 0x004012B8 bypasses it. To go into calls we must change JE on NOP. (JE is depends on system time. For more information, look procedure at address 0x0040149E).
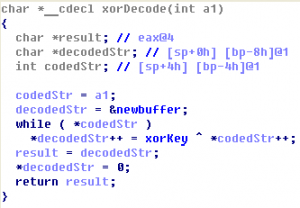
Function at address 0x00401070 decodes string with flag (XOR algorithm).
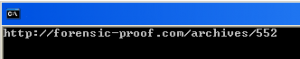
Procedure at address 0x004010C0 prints answer in the console: