You can find all photo in our album
Tag: leetmore
Aug 09
Lockpicking in Las Vegas
Sep 22
Leet More 2010 Lottery writeup
Warning! There are at least two ways of solving this task. Look at HTML sources. Try to find web-framework running the lottery. It is “Nitrogen”- Web Framework for Erlang. To generate random numbers Erlang have module random. To get random Int we have function uniform(MaxInt)->Int So example of code for generating number for lottery is …
Sep 21
Leet More 2010 LameHackers writeup
Category: crypto Greetings from LameHackers Inc.! We have hacked into the internal Pentagon computer system and managed to steal their text-file-where-they-keep-the-root-password. But the password doesn’t work :( Can you help us? File Ok, first of all I want to thank everyone participating in Leet More 2010, it was a cool competition, though on wednesday. And …
Sep 21
Leet More 2010 Oh Those Admins! writeup
Category: web-vuln?! http://vos.uz/oh_those_admins/ http://vos.uz/oh_those_admins/index.php.txt The php script takes a ‘password’ as input, calculates its raw (binary) md5, performs SQL query: SELECT login FROM admins WHERE password = ‘$raw_md5′ and if it returns something, gives us full list of admins. Raw md5 can contain any chars, and script puts them in query as is – it’s …
Sep 21
Leet More 2010 Jailbreak writeup
Category: CTB A piece of code is currently up @ ctf.ifmo.ru:4004 BTW, here is what’s inside the jail: vos@ms7:~/private_data$ ls -la total 20K d——r-x 2 alice alice 4.0K Aug 21 00:23 . d——r-x 3 alice alice 4.0K Aug 21 00:29 .. ——-r– 1 alice alice 9.0K Aug 21 00:23 key Ok, we have this binary …
Sep 21
Leet More 2010 brainfffuuuuu writeup
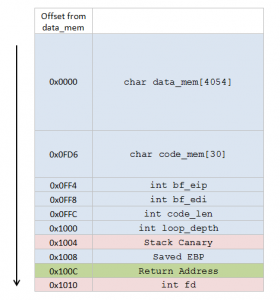
Category: CTB This binary is running at ctf.ifmo.ru Are you able to get the key?! Let’s take a look at what the binary is doing (decompilation of its main function begin_the_fucking() will help us): 1. Prints out some prompt 2. Reads 30 bytes 3. Interprets them as Brainfuck code. and here is what the stack …
Sep 21
Leet More 2010 SHAdow dROP writeup
Category: reverse Generate a license! shadowdrop.exe Lets start with examining the binary. It installs a SEH handler with “bad guy” message, pushes some binary trash on the stack, opens “license.key“, and for each 5 bytes in reads from license, it calculates their SHA-1 and xors another 20 bytes on stack with hash binary. After xoring …
Sep 15
Leet More 2010 ELF Quest writeup
Find the hidden message. file Try the file tool and u’ll be told it is an ELF file. But any other tools say the header is corrupted and if you compare it with true ELF header, you will know it’s a trash. A good thing for further analysis is to count chars. 73 30 6d …
Sep 15
Leet More 2010 Time Traveller writeup
A scientist who worked on the issue of space-time continuum, suddenly disappeared. He left only a mysterious drawing in a notebook. There is a suspicion that he traveled back in time. In what year did he travel? And what is his name? There are only 2 breaks in this maze. Let’s try to find the …
Sep 15
Leet More 2010 Strange Cipher writeup
Decrypt this “UPDYUFFRPY\TDDSUITF\R\FARTTITYGPPF\/YSGDFYAAO:DF/TA\IAGR:A//DR/T”. ctf.ifmo.ru:5555 If we connect to the service and try to encrypt \x00, \x01, \x02, \x03, \x04, we can notice that only first two bytes and the last one change: [ GDOPU/SIIR\TDPAFYGDA/:S/EIT\\FS/OA:PRYS/DOIOTIS/GUPPYPS/GIGPUSS\ ] [ GFOPU/SIIR\TDPAFYGDA/:S/EIT\\FS/OA:PRYS/DOIOTIS/GUPPYPS/GIGPUSSE ] [ GGOPU/SIIR\TDPAFYGDA/:S/EIT\\FS/OA:PRYS/DOIOTIS/GUPPYPS/GIGPUSSR ] [ ::OPU/SIIR\TDPAFYGDA/:S/EIT\\FS/OA:PRYS/DOIOTIS/GUPPYPS/GIGPUSST ] There are 16 different chars, so a good idea is to …
Sep 15
Leet More 2010 Noise Magic writeup
I think there’s nothing interesting in this image. Do you agree? image The image looks like it’s just a random noise. To make sure, we can measure a randomness. Pixels of each color can appear in each place of the image with equal chance. If it’s false for some colors, we certainly want to look …
Sep 14
Leet More 2010 Stack or what? writeup
We received a new CPU model, you are to make a vulnerability check. Enter the CPU secret code as a proof. [ ctf.ifmo.ru:3123 ] + binary Here we have a VM with a few instuctions: nop, add, xor, mul, push, pop, loop, pops, pushs and core. The most intresting is core – it spawns a …