Category: crypto
Greetings from LameHackers Inc.!
We have hacked into the internal Pentagon computer system and managed to steal their text-file-where-they-keep-the-root-password.
But the password doesn’t work :( Can you help us?
File
Ok, first of all I want to thank everyone participating in Leet More 2010, it was a cool competition, though on wednesday. And ofc congrats to Nibbles for the 1st place ;)
Now, to the writeup.
The task RAR archive contains two files:
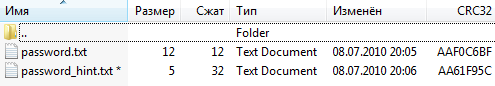
password.txt‘s content is “VVoimlC0L7XC” (which is not the answer), and password_hint.txt is encrypted with a rar password.
There is no known attacks on rar encryption besides bruteforce, and it gives us nothing, so instead of attacking encryption, we’ll attack “side channel”.
Password hint is only 5 bytes long, and we know its CRC32 checksum (AA61F95C). Math tells us there are a few possible 5-byte combinations that give this crc. Let’s bruteforce them.
I’m using MDCrack to do this, and i’ve experimented to find out that its CRC32-B algorithm is the same that WinRAR uses. We also need to reverse the byte order of crc.
> MDCrack-sse.exe --algorithm=CRC32-B --charset=%N%U%L%P \ --minsize=5 --maxsize=5 --all 5CF961AA System / Starting MDCrack v1.8(3) <...> System / Thread #0: Collision found: C<->7 <...> System / Thread #1: Collision found: ~-aVo <...> System / Thread #1: Collision found: _sq?# <...> System / Thread #0: Collision found: bb=W{
Long story short, “C<->7” is what we need (exchange Cs and 7s).
“VVoimlC0L7XC” + “C<->7” = “VVoiml70LCX7“, the answer.
More write-ups on “LameHackers”:
