Category: exploiting
You have seen a deserted space station. Your task is to enter it. The first barrier is the access system. But you can find a module with the application on it. Here is the file:
What is the key?
(There is also station A, but station B is the advanced one.)
Summary: patching smali code for debug output
Let’s use Android SDK to run the app:
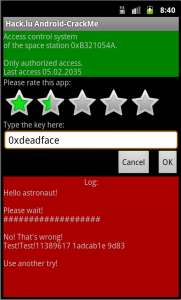
After playing with it a bit, we see that we can rate it (from 0 to 5 with step 0.5) and put a dword in text field (like in Space Station 0xA1EA512A).
So, let’s reverse it! First we should unzip apk file, then run dex2jar, extract jar file and decompile .class files with jd-gui or jad.
But getting decompiled Java code doesn’t help much. There is a huge algorihtm there, checking different conditions and printing various messages. There are some hardcoded dwords like 0x1adcab1e, 0x1badbabe, 0xdeadbef7 but they aren’t right answers.
I decided to add debugging output to each condition check. It can’t be done on Java code level, because we have no sources. It can be done on smali code. I saw it for the first time but it’s not very hard to find out how to add messages – we can just copy existing block of code.
To decompile and compile the package, we’ll use apktool and Apk Manager for signing and installing it on Android.
Here’s a template code for debug output:
# --------------------------------------------- const-string v99, "cmp(rate,3.5)=" move-object v0, v14 move-object/from16 v1, v99 invoke-virtual {v0, v1}, Landroid/widget/TextView;->append(Ljava/lang/CharSequence;)V move/from16 v0, v21 invoke-static {v0}, Ljava/lang/Integer;->toHexString(I)Ljava/lang/String; move-result-object v1 move-object v0, v14 invoke-virtual {v0, v1}, Landroid/widget/TextView;->append(Ljava/lang/CharSequence;)V const-string v99, "; " move-object v0, v14 move-object/from16 v1, v99 invoke-virtual {v0, v1}, Landroid/widget/TextView;->append(Ljava/lang/CharSequence;)V # ---------------------------------------------
I inserted it before each if statement I found, adapting to different types.
Final smali code, package.
Now, if you run patched apk:
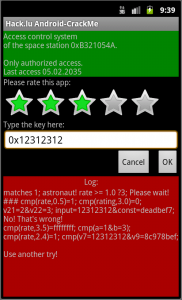
We see that the last check is done only when rate is greater than 2.5, and input is compared with 0x8c979bef when rate is 3.0. But if we put it in the text field, it’s replaced with 0x9d83.
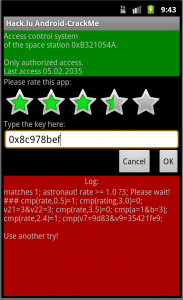
If we try different rates, we’ll find another dword at rate 3.5:
When we put in in the text field, the app says OK.
And this flag is accepted.
The flag: 0x35421fe9