Program is not packed x86 executable PE file.
binary
After analyze winmain function, you can see, that it is mostly anti-debug code:
IsDebugProcess = 0; kernel32_base = 0; rdtsc_low = 0; rdtsc_high = 0; rdtsc_high2 = 0; kernel32_base = getKernel32Base(); printf("Enter key: "); for ( i = 0; i < 0x30; ++i ) { stdin = _iob_func(); new_symb = fgetc(stdin); if ( (signed int)(unsigned __int8)new_symb < '0' || (signed int)(unsigned __int8)new_symb > '9' ) { if ( (signed int)(unsigned __int8)new_symb < 'a' || (signed int)(unsigned __int8)new_symb > 'f' ) break; } pass[i] = new_symb; } AntiDebugRdtsc(&rdtsc_high, &rdtsc_low); IsDebugProcess = (int (*)(void))GetIsDebugger(0xA36DC676u, kernel32_base, LoadLibraryW, GetProcAddress); if ( i == 0x30 && IsDebugProcess() <= 0 ) { v3 = 245 * (IsDebugProcess() + 3); i = (unsigned int)dword_40F000; AntiDebugRdtsc(&rdtsc_high2, &rdtsc_low); i += 32 * (rdtsc_high2 - rdtsc_high + 3); do result = i + 337; while ( i == 0xAF ); } else { printf("Invalid key"); result = -1; } |
The main check function begin at 0x004011CD
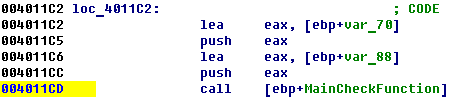
And go to 0x4042e6
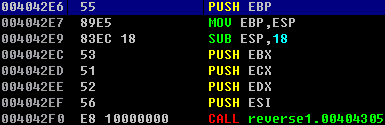
After that long mutation code begins. One function un pack another and so on and so far:
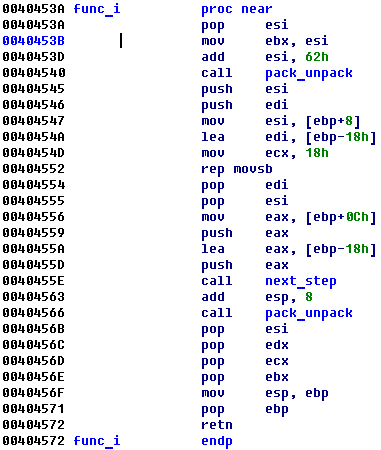
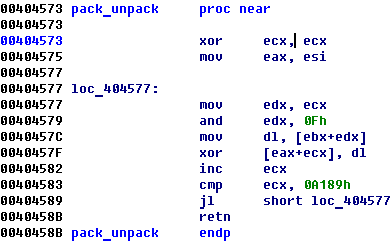
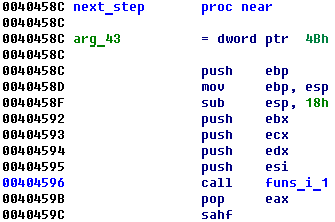
It is continuing until 0x40b3e3 where you will find main check algorithm:
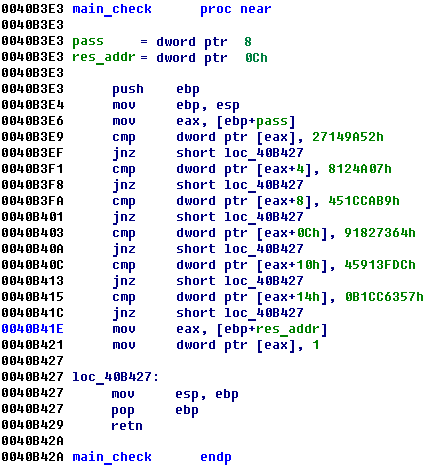
So from that we can reconstruct code and got the back account:
C:\ctf\ictf\challenge_29>reverse1.exe
Enter key: 529a1427074a1208b9ca1c4564738291dc3f91455763ccb1
Bank account: 2526390575284-60846167886

1 comment
1 ping
Nice! Just keep it coming :-)
[…] More (Challenges 29, 30, 31, 32, […]