In a recent battle we took an enemy robot hostage and examined his operating system. During the examination we found a piece of robot malware that we don’t quite understand. Can you enumerate its targets?
This challenge was made by our friends at ManTech. If you enjoyed it, you might be interested in working for them.
Summary: unpack x64 ELF, bot request analysis.
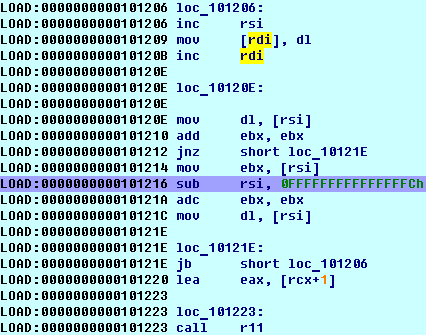
A file is packed x64 ELF. An unpack algorithm is easy. Set hardware breakpoint at read/write encrypted memory (for example 0x01001A0) and find that program unpack itself to allocated memory.
An unpacking procedure :
Allocated memory:
If you dump allocated memory after unpacking you will find unpacked file. Even though, unfortunately, all references to curl functions (and any lib functions) is invalid, unpacked file is small, and we can easily analyze it.
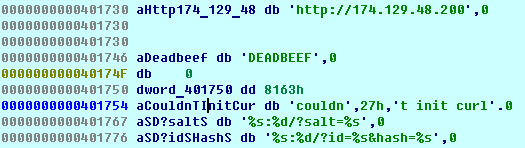
First of all, check strings:
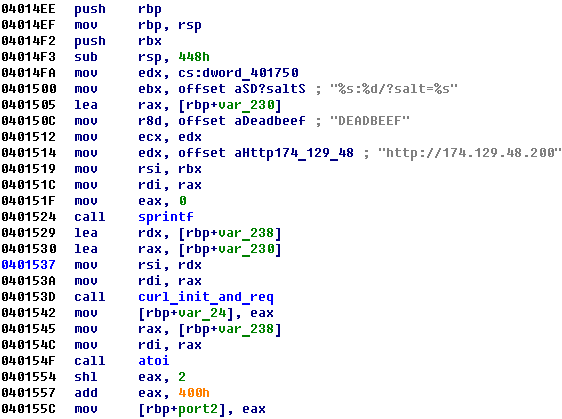
It looks like parts of HTTP request strings. So, the file seems to be a bot which does two HTTP requests. A first request performs to take a port number for a second request.
port2 = answer*4 + 0x400
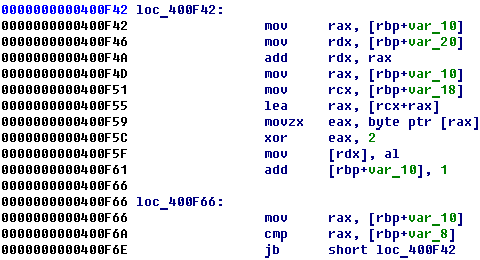
After that, program calculates a hash from id = “1337” and create a base64 string from this hash.
The hash is calculated by easy formula from id. It xors each byte of id with 2 and base64s result.
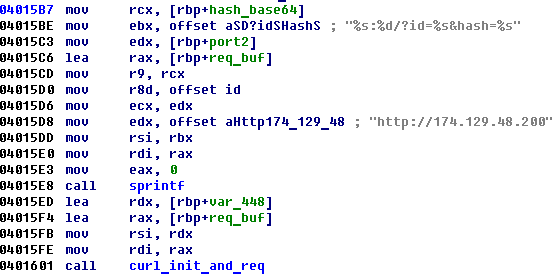
Then, the program constructs and performs a second request:
There is an example of second request:
Because we know that we can put any id in request. We tried easy sqli and it worked:
GET /?id=>1’%20or%201%20–&hash=PDMlIm1wIjMiLy8= HTTP/1.1
Host: 174.129.48.200:5555
Accept: */*
Notice: a server incorrectly processes space symbol, so we should send
id = “>1’%20or%201%20–&” but
hash = calc_hash(“>1′ or 1 –”)
Key: Pwning1$m0reFunWhenTargetsBounce
Exploit here.


2 comments
1 ping
port2 = answer*2 + 0×400
I think it’s :
port2 = (answer << 2) + 0x400
Author
For sure, you are right. Thank you for attention, I fixed it.
[…] http://leetmore.ctf.su/wp/plaidctf-2012-…l-packets/ […]