This challenge was on remote exploiting. The binary is for SunOS (Solaris). binary Summary: shellcoding challenge
Tag: binary
Jun 06
Defcon CTF Quals 2011 – Pwnables 400
This challenge was on remote exploiting. The binary is for Linux, statically linked and stripped. binary Summary: overflow, ROP for execve(“/bin/sh”)
Apr 27
PlaidCTF 2011 #23 – Exploit Me :p (200)
Category: pwnables It seems like AED also has some plans to raise hacker force! We found this binary as an exploitation practice program in the office, but they forgot to remove the setgid flag on the program. So we can get the secret key! ssh username@a5.amalgamated.biz Username: exp_1 Password: jNKpzFuRLpsIW9xzqNIpCVF1 Summary: .dynamic->FINI overwriting, execl symlink …
Apr 27
PlaidCTF 2011 #19 – Another small bug (250)
Category: pwnables This time, let’s attack /opt/pctf/z2/exploitme. ssh username@a5.amalgamated.biz Username: z2_1 Password: 29rpJinvpwoI7pzdufQc4h6edzvyh Summary: buffer overflow, static binary binary
Apr 27
PlaidCTF 2011 #18 – A small bug (250)
Category: pwnables Get access to the key using /opt/pctf/z1/exploitme. ssh username@a5.amalgamated.biz Username: z1_1 Password: GwB4eivw9NTvCjmobw1EnuyqcWfJs Summary: race condition, create a symlink before the file is opened binary
Apr 26
PlaidCTF 2011 #20 – C++ upgrade (300)
Category: pwnables They have an update for the vulnerable C++ program trying to fix the bug. However, the coders at AED suck and introduced another stupid mistake. Get a shell (and the key, too.) ssh username@a5.amalgamated.biz Username: cpp2_1 Password: zKQaKrdFPSsT6j03XSt31NaT0H Summary: tricky overflow class’ method and exec’ing symlinks binary
Apr 26
PlaidCTF 2011 #17 – C++5x (300)
Category: pwnables AED decided to use C++ to develop their internal tools. However, they seem to make a mistake one of their new C++ programs. Exploit and get the key! ssh username@a5.amalgamated.biz Username: cpp1_1 Password: IwKheuEHvR1jYXmjIYz8bo8FFe1h8 Summary: tricky overflow class’ method and exec’ing symlinks binary
Mar 08
Codegate CTF 2011 Binary 200
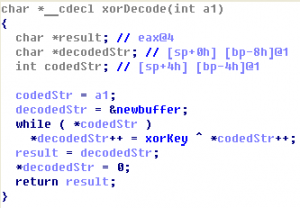
Let’s open this PE-file in IDA Pro. There is TLS-callback at address 0x00401450. TLS-callback is just anti-debugging trick (with SEH, dynamic import etc), so we can skip it and start execution from entry point: 0x00401000. On the entry point we can see some decoding cycle and one call at address 0x00401058. If we go into …
Mar 08
Codegate CTF 2011 Issue 500 (bootsector)
Find a key. [link to submit form] binary $ file challenge.bin challenge.bin: x86 boot sector, code offset 0xc0 Summary: bootsector with password check, bruteforcing 2 bytes hash.
Jan 20
Padocon CTF 2011 Binary500 Writeup (300)
The challenge consists of a windows binary and connection details: HOST : 168.188.130.216 PORT : 888 Binary (Daemon.exe) Summary: reversing the algorithm with some encryption and coding a client
Jan 19
Padocon CTF 2011 Binary100 Writeup (200)
This task we were given a binary and a host/port where it is running: HOST : 168.188.130.217 PORT : 8080 Binary Note: At the beginning of the contest, there was no binary. But nobody solved it and the binary was added, I guess it’s because of strange format of the input. Summary: reversing (or guessing) …
Nov 02
Hack.lu 2010 CTF #22 (Pirates Wisdom) writeup
Pirates Wisdom Captian Iglo heard there is a secret wisdom in the well known pirate wisdom system. Log in to ssh pirates.fluxfingers.net:9022 user: ctf password: ctf and get the content of key.txt. You get rewarded with 300 coins. binary Summary: simple heap’s chunk reusage error with a bit obfuscated logic
- 1
- 2