It seems easy, right? rsa.zip Tip: openssl rsautl -encrypt -in FLAG -inkey public.pem -pubin -out flag.enc Summary: factoring 300-bit modulus into 3 primes, extracting cube roots.
Category: Writeups
Mar 07
Boston Key Party CTF 2016 – GCM (Crypto 9pts)
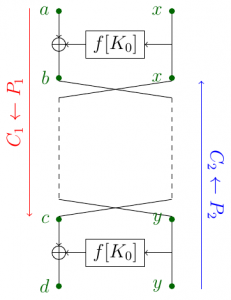
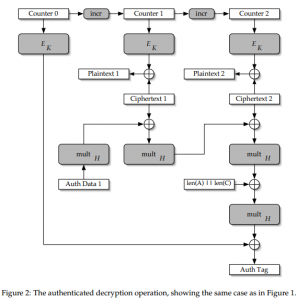
[8] : gsilvis counting magic – 9 – 4 solves : crypto: Here’s a verification/decryption server: gcm.ctf.bostonkey.party:32768 . Get the GCM MAC key (the thing the server prints out on startup). We’ve given you one valid ciphertext to get you started. It has iv: [102 97 110 116 97 115 116 105 99 32 105 …
Mar 07
Boston Key Party CTF 2016 – HMAC-CRC (Crypto 5pts)
[3] : hmac_crc – 5 – 36 solves : crypto: We’re trying a new mac here at BKP—HMAC-CRC. The hmac (with our key) of “zupe zecret” is ‘0xa57d43a032feb286’. What’s the hmac of “BKPCTF”? hmac-task.py Summary: breaking HMAC-CRC (again)
Sep 07
MMA CTF 2015 – Motto Mijikai Address (Crypto/Web 100+300)
Login as admin and get the flag1. mmaddress.7z Summary: breaking HMAC-CRC512
May 27
CONFidence CTF 2015 – RSA2 (Crypto 500)
Find the flag data Summary: cube attack + recover python’s MersenneTwister state + leak 320/520 LSBs of one of the primes
May 04
VolgaCTF Quals 2015 – CPKC (Crypto 400) writeup
cpkc A home-brewed cryptosystem, should be easy to break. Its keyspace seems to be rather large though… challenge.tar Summary: LLL-based attack on NTRUEncrypt-like cryptosystem.
Apr 19
PlaidCTF 2014 parlor writeup
The Plague is running a betting service to build up funds for his massive empire. Can you figure out a way to beat the house? The service is running at 54.197.195.247:4321.
Apr 18
PlaidCTF 2014 __nightmares__ writeup
The Plague is building an army of evil hackers, and they are starting off by teaching them python with this simple service. Maybe if you could get full access to this system, at 54.196.37.47:9990, you would be able to find out more about The Plague’s evil plans. Code: (can be run locally with $ socat …
Apr 17
PlaidCTF 2014 RSA writeup
Our archaeologists recovered a dusty and corrupted old hard drive used by The Plague in his trips into the past. It contains a private key, but this has long since been lost to bitrot. Can you recover the full key from the little information we have recovered?
Mar 02
Boston Key Party CTF – Differential Power (Crypto 400)
we hooked up a power meter to this encryption box. we don’t know the key. that’s what we want to know. you can encrypt any string of 8 characters on the service http://54.218.22.41:6969/string_to_encrypt encrypt.asm chall source (released after ctf)
Feb 24
Codegate 2014 Quals – Angry Doraemon (pwn 250)
□ description ========================================== OS : Ubuntu 13.10 x86 IP : 58.229.183.18 / TCP 8888 http://58.229.183.26/files/angry_doraemon_c927b1681064f78612ce78f6b93c14d9 ========================================== □ number of solvers : 57 □ breakthrough by 1 : More Smoked Leet Chicken (02/23 06:16) 2 : ppp (02/23 06:22) 3 : stratumauhuur (02/23 06:28) Binary