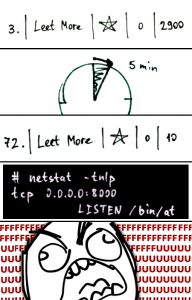
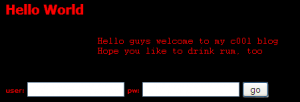
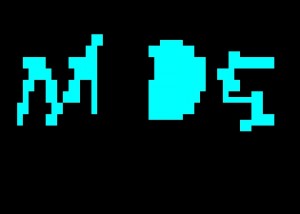On the high seas, the nights get boring. Try to win the game against the captain! pirates.fluxfingers.net port 6565/tcp Let’s go & connect there: > nc pirates.fluxfingers.net 6565 /9j/4AAQSkZJRgABAQEAYABgAAD//gAJbWQ1d2luc//bAEMABQ MEBAQDBQQEBAUFBQYHDAgHBwcHDwsLCQwRDxISEQ8RERMWHBcT <…> EgWAYlOhQqadCpxQPCn4JDjQoVacgqCQ4dtCAY4+FChVJb7BVE A6fCnKIB0+FChSuX3C8XQPuhoUKFd+JM//Z The service gives us some base64 and waits 2 seconds for reply. Unbase64ing the data, we get this jpeg: There is no …
Continue reading