This challenge was on reverse engineering. The binary is 32bit MZ-PE executable for Windows.
Summary: reverse engineering, anti-anti-debugging challenge
At first glance, the sample is not packed, but let’s look at imports, there are only three ones:
- CloseHandle
- HeapAlloc
- memset
So, it means than it gets them dynamically. We can easily find this part of code, there is immediately after OEP. The sample gets all needed API from PEB by hash.
After that, the sample creates couple of thread with anti-debug functionality (0x00401930). There are some tricks like:
- NtQueryInformationProcess with (push 1eh ;ProcessDebugObjectHandle)
- Rdtsc check
- NtSetInformationThread with (push 11h ; ThreadHideFromDebugger)
and so on.
It is not so easy outflank them (you need some skill for that), but it is easy to find information about them in google :)
Or you can find a description here and here
After all, the most interesting part execute in allocated memory (really it is copied to allocated memory from 0x0403000).
You can find the gate to this code in function at 0x00401eb0:
If you just executed that memory you would get a decrypted information block with couple of “philosophy quotes”:
- In the beginner’s mind there are many possibilities, but in the expert’s mind there are few.
- No snowflake ever falls in the wrong place.
- The obstacle is the path.
- The tighter you squeeze, the less you have.
- To know and not do is not yet to know.
- When the pupil is ready to learn, a teacher will appear.
- Always remember that you’re unique. Just like everyone else.
- Never test the depths of the water with both feet.
- If you think nobody cares if you’re alive, try missing a couple of car payments.
- If at first you don’t succeed, skydiving is not for you.
- If you lend someone $20 and never see that person again, it was probably worth it.
- If you tell the truth, you don’t have to remember anything.
- Some days you’re the bug, some days you’re the windshield.
- Everyone seems normal until you get to know them.
- The quickest way to double your money is to fold it in half and put it back in your pocket.
- A closed mouth gathers no foot.
- There are two theories to arguing with women. Neither one works.
- Generally speaking, you aren’t learning much when your lips are moving.
- Never miss a good chance to shut up.
- Those who know don’t tell and those who tell don’t know.
Ohh good, there is an answer? Hah, not so easy, it is not binary 100 at all :) Slew some anti-debug tricks and get a memory dump are not enough.
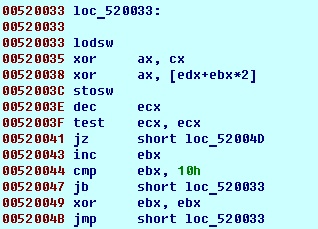
Ok, try to analyze algorithm. Curiously enough it is pretty easy, just xor
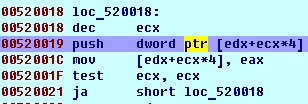
But there is also one interesting place in code, before decrypt function, parameters are pushed into stack and removed from allocated memory:
It is why if you just made memory dump after executing, you would get this instead of decrypt keys:
If you did it before erasing you would get another memory:
So, key is
2FE3903DF19E4B01AC590FBA671DC8752BD68339E49147F29F5502AD6310BB71