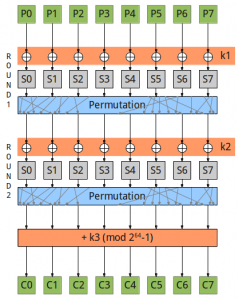
0ops Toy Cipher, hope you enjoy it:) zer0TC.zip Summary: meet-in-the-middle and key-schedule constraints
Tag: permutation
Oct 25
Hack.lu 2013 CTF – Crypto 350 (BREW’r’Y)
BREW’r’Y (Category: Crypto) Author(s): dwuid Finally, the robots managed to sneak into one of our breweries. I guess I won’t have to explain how bad that really is. That darn non-physical ones even shutdown our login system. Shiny thing, advanced technology, all based on fingerprints. Been secure as hell. If only it was running. Well, …
Apr 04
Nuit du hack 2011 CTF Crypto 300
Crypto300 (150 pts.) source Python source code is very clear and concise, and could sometimes bring out lots of clues. This is particularly true for this challenge. Summary: key exchange algorithm based on permutations (braid based cryptography), has some vulnerabilities