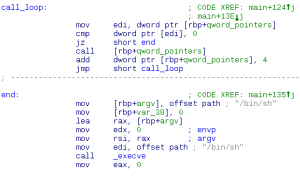
good luck. penser.shallweplayaga.me:8273 http://assets-2013.legitbs.net/liabilities/penser Download penser binary » Summary: x86_64 Unicode-proof shellcoding.
Tag: shellcode
Jun 17
Defcon CTF Quals 2013 – \xff\xe4\xcc 3 (linked)
typedef struct _llist { struct _llist *next; uint32_t tag; char data[100]; llist; and: register char *answer; char *(*func)(); llist *head; … func = (char *(*)(llist *))userBuf; answer = (char *)(*func)(head); send_string(answer); exit(0); Write me shellcode that traverses the randomly generated linked list, looking for a node with a tag 0x41414100, and returns a pointer to …
Oct 25
Hack.lu 2012 CTF Challenge #14-15 (150+250)
14 – Safehouse It’s the middle of the night. Nothing but complete darkness and the moaing of approaching zombies surrounds you. You need to escape. Fast. There seems to be nothing to hide and nowhere to run. But then – a small dancing gleam appears while you are running through the blackness. Could it be? …
Feb 26
CodeGate 2012 Quals – Vuln 300
Here we are given ssh credentials where we need to exploit the binary. Summary: compose file to make program jump to stack.
Jun 07
Defcon CTF Quals 2011 – Pwnables 100
This challenge was on remote exploiting. The binary is for FreeBSD. binary Summary: buffer overflow, jump to shellcode (bruteforce address)
Jun 06
Defcon CTF Quals 2011 – Pwnables 200
This challenge was on remote exploiting. The binary is for SunOS (Solaris). binary Summary: shellcoding challenge
Apr 27
PlaidCTF 2011 #19 – Another small bug (250)
Category: pwnables This time, let’s attack /opt/pctf/z2/exploitme. ssh username@a5.amalgamated.biz Username: z2_1 Password: 29rpJinvpwoI7pzdufQc4h6edzvyh Summary: buffer overflow, static binary binary