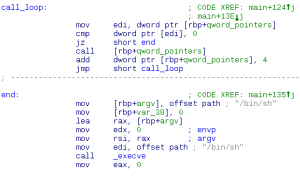
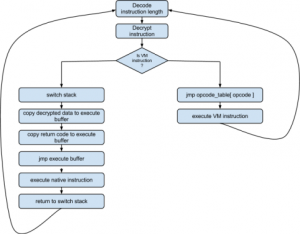
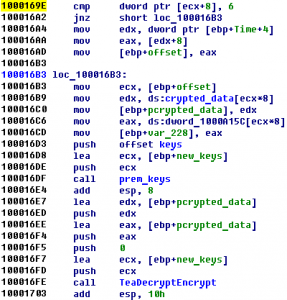
Talent Yang loves to customize his own obfuscator. Unfortunately, he lost his seed when he was watching Arsenal’s UEFA game. What a sad day! His team and his seed were lost together. To save him, could you help him to get back his seed? We can not save the game, but we may be able …
Tag: binary
Feb 02
Olympic CTF Sochi 2014 Registration is Open
Let there be Olympics MSLC proudly presents…Alright, do we even need words here? Game starts: February 7th, 2014 16:14 UTC (yeah yeah, those Sochi number freaks… it’s 20:14 in MSK timezone) Game ends: February 9th, 2014 16:14 UTC Sign up: https://olympic-ctf.ru/ Prize set: 1500 USD, 1000 USD, 500 USD. Expect decent tasks. Twenty of them.
Jun 17
Defcon CTF Quals 2013 – \xff\xe4\xcc 4 (penser)
good luck. penser.shallweplayaga.me:8273 http://assets-2013.legitbs.net/liabilities/penser Download penser binary » Summary: x86_64 Unicode-proof shellcoding.
Oct 25
Hack.lu 2012 CTF Challenge #14-15 (150+250)
14 – Safehouse It’s the middle of the night. Nothing but complete darkness and the moaing of approaching zombies surrounds you. You need to escape. Fast. There seems to be nothing to hide and nowhere to run. But then – a small dancing gleam appears while you are running through the blackness. Could it be? …
May 01
SIMD [250] (Pirating)
After examining some code retrieved by our operative we are unsure whether it was written by an evil genius or a google employee. We will let you decide. Summary: linux x64 binary, obfuscated xor
Feb 27
CodeGate 2012 Quals – Binary 300
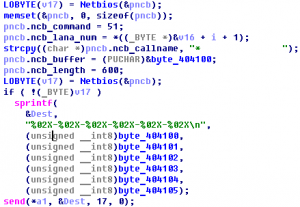
There are malicious program associated with DDoS zombie. Calcurate the sum of port numbers used for the attack. And, how many times does zombie try to attack? Answer: sum(attack_ports) * attack_count (* : multiplication) Download : 72C4DAA981E17282B12E6226A1D60162 Summary: unpack, malware analyse
Feb 26
CodeGate 2012 Quals Vuln500 Write-up
1.234.41.7:22 ID : yesMan PWD : ohyeah123 Download vulnerable binary. Vuln500 was a hardened format-string vuln with ASLR, NX-stack, no-DTORs, RO .dynamic
Feb 26
CodeGate 2012 Quals – Binary 200
Find a printable string that the program would print ultimately. Down (pw: infected) Summary: unpack, XTEA decrypt
Feb 13
IFSF CTF 2012 #9 – X97
SSH : 208.64.122.235 guest:guest binary Category: exploitation Summary: format string bug, ASLR and NX
Sep 21
hack.lu CTF 2011 Antique Space Shuttle (300)
Category: exploiting Your command is to get as much information about the crew of an antique space shuttle. We know our acient father used finger as reference point at nc ctf.hack.lu 2003 Summary: bash injection, and buffer overflow on a suid binary to get more privilegies
Jun 09
Defcon CTF Quals 2011 – Retro 400
This challenge was on remote exploiting. The binary is for FreeBSD. The program is some kind of a Virtual Machine, with it’s own stack and memory. binary Summary: memory address check mistake, write shellcode and overwrite _exit function pointer
Jun 07
Defcon CTF Quals 2011 – Pwnables 100
This challenge was on remote exploiting. The binary is for FreeBSD. binary Summary: buffer overflow, jump to shellcode (bruteforce address)
- 1
- 2