Oh great shaman! Somehow the village idiot got his hands on this fancy control machine controlling things. Obviously, we also want to control things (who wouldn’t?), so we reverse-engineered the code. Unfortunately, the machine is cryptographically protected against misuse. Could you please maybe spend a few seconds of your inestimably valuable time to break that …
Tag: crypto
Oct 02
TUM CTF 2016 – ndis (Crypto 300)
We have a HTTPS server and client talking to each other with you right in the middle! The client essentially executes curl –cacert server.crt https://nsa.gov with some magic to redirect the transmitted data to your socket, to which the server responds with a lovely German-language poem. NOTE: There is nothing else hosted on the server; …
Sep 05
Tokyo Westerns/MMA CTF 2016 – Backdoored Crypto System (Reverse+Crypto 400)
Get the flag. bcs.7z $ nc bcs.chal.ctf.westerns.tokyo 3971 Summary: recovering AES key from partial subkey leaks.
Sep 05
Tokyo Westerns/MMA CTF 2016 – Pinhole Attack (Crypto 500)
Decrypt the cipher text with a pinhole. $ nc cry1.chal.ctf.westerns.tokyo 23464 pinhole.7z Summary: attacking RSA using decryption oracle leaking 2 consecutive bits in the middle.
May 03
Google CTF – Woodman (Crypto 100)
How honest are you? Running here Summary: breaking a weak PRNG
May 01
Google CTF – Spotted Wobbegong (Crypto 100)
Are you able to defeat 1024-bit RSA? public.pem Summary: breaking RSA with PCKS v1.5 padding and exponent 3.
May 01
Google CTF – Jekyll (Crypto)
Can you access the admin page? You can look at the crypto here. source.py Summary: finding a preimage for a simple 64-bit ARX-based hash.
May 01
Google CTF – Wolf Spider (Crypto 125)
Continuing on from Eucalypt Forest – can you break Message Authentication in Wolf Spider wolf.py Summary: forging signatures by exploiting CBC padding oracle and hash length extenstion
Apr 24
PlaidCTF 2016 – sexec (Crypto 300)
If you need to securely grant execution privileges, what better way to do it than sexec? This is running on sexec.pwning.xxx:9999 sexec.tar.gz Summary: attacking a small instance of Ring-LWE based cryptosystem with Babai’s Nearest Vector algorithm.
Apr 18
PlaidCTF 2016 – Radioactive (Crypto 275)
We just got this fancy new cryptographic device and it seems to work great… for the most part. But sometimes the values it gives me are wrong. Maybe you could take a look for me. radioactive.tar.bz2 Summary: fault attack on RSA signature (not RSA-CRT)
Mar 14
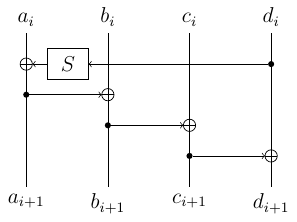
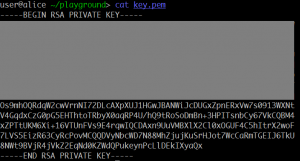
0CTF 2016 Quals – Equation (Crypto 2 pts)
Here is a RSA private key with its upper part masked. Can your recover the private key and decrypt the file? equation.zip Summary: recovering RSA key from part of the private key.
Mar 13
0CTF 2016 Quals – RSA? (Crypto 2 pts)
It seems easy, right? rsa.zip Tip: openssl rsautl -encrypt -in FLAG -inkey public.pem -pubin -out flag.enc Summary: factoring 300-bit modulus into 3 primes, extracting cube roots.
Sep 07
MMA CTF 2015 – Motto Mijikai Address (Crypto/Web 100+300)
Login as admin and get the flag1. mmaddress.7z Summary: breaking HMAC-CRC512
May 27
CONFidence CTF 2015 – RSA2 (Crypto 500)
Find the flag data Summary: cube attack + recover python’s MersenneTwister state + leak 320/520 LSBs of one of the primes