In a recent battle we took an enemy robot hostage and examined his operating system. During the examination we found a piece of robot malware that we don’t quite understand. Can you enumerate its targets? This challenge was made by our friends at ManTech. If you enjoyed it, you might be interested in working for them. Summary: unpack …
Tag: ctf
Mar 26
NuitDuHack 2012 Prequals – Web3.ndh
Our spy thinks that Sciteek staff is aware about the mole inside their building. He is trying to read a private file named “sciteek-private.txt” located at sciteek.nuitduhack.com:4005. Please find the .ndh attached, if you are sucessfull, reply with a message entitled “complex remote service”. Of course, your efforts will be rewarded with $2500. Maybe you …
Mar 26
NuitDuHack 2012 Prequals – executable1.ndh
Meanwhile, we got fresh news from our mystery guy. He came along with an intersting binary file. It just looks like an executable, but it is not ELF nor anything our experts would happen to know or recognize. Some of them we quite impressed by your skills and do think you may be able to …
Mar 26
NuitDuHack 2012 Prequals – sciteekadm.cap
Hopefully, we succeeded to spy some wireless communications around Sciteek building, our technical staff has attached the capture file, will you be able to exploit it? We hope that some valuable files were exchanged during the capture. Please entitle your reply “captured file”, as usual. By the way, your account has been credited with $1000. …
Mar 26
NuitDuHack 2012 Prequals – executable2.ndh
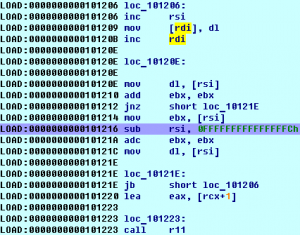
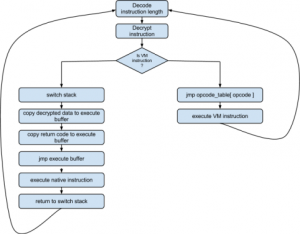
Our anonymous guy managed to get access to another bunch of files. We also need to get as much information as possible about the file itself. If you succeed, you will be rewarded with $2500 for the ndh file. executable2.ndh NDH Virtual Machine Summary: VM in the NDH VM, crackme
Feb 27
CodeGate 2012 Quals – Binary 300
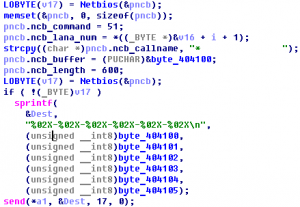
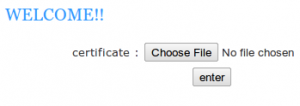
There are malicious program associated with DDoS zombie. Calcurate the sum of port numbers used for the attack. And, how many times does zombie try to attack? Answer: sum(attack_ports) * attack_count (* : multiplication) Download : 72C4DAA981E17282B12E6226A1D60162 Summary: unpack, malware analyse
Feb 26
CodeGate 2012 Quals – Vuln 300
Here we are given ssh credentials where we need to exploit the binary. Summary: compose file to make program jump to stack.
Feb 26
CodeGate 2012 Quals – Vuln 200
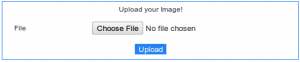
This web challenge is again about uploading. Our aim was to get shell. Summary: upload php shell, read the key.
Feb 26
CodeGate 2012 Quals – Vuln 100
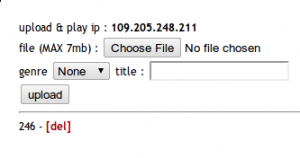
This challenge is a web service where one can upload mp3 files and listen to them. Our aim is to get admin’s song. Summary: sql injection
Feb 26
CodeGate 2012 Quals – Binary 200
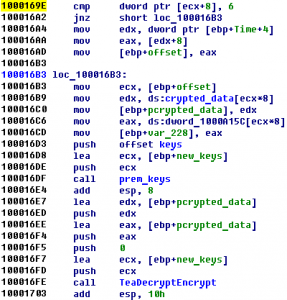
Find a printable string that the program would print ultimately. Down (pw: infected) Summary: unpack, XTEA decrypt
Feb 13
IFSF CTF #7 (X99) Write-up
this is one of their machines which have very sensitive informations , try to get for us the password 208.64.122.27 PORT : 3000 X99 carries a synthetic vulnerability that allows a char-by-char password bruteforce.
Feb 13
IFSF CTF Small Challenges (#4, #5, #6, #14, #15)
Contents #4 ER #5 Change #6 Call me #14 Seek me #15 Embedded docs