Continuing on from Eucalypt Forest – can you break Message Authentication in Wolf Spider wolf.py Summary: forging signatures by exploiting CBC padding oracle and hash length extenstion
Tag: writeup
Apr 24
PlaidCTF 2016 – sexec (Crypto 300)
If you need to securely grant execution privileges, what better way to do it than sexec? This is running on sexec.pwning.xxx:9999 sexec.tar.gz Summary: attacking a small instance of Ring-LWE based cryptosystem with Babai’s Nearest Vector algorithm.
Mar 14
0CTF 2016 Quals – Equation (Crypto 2 pts)
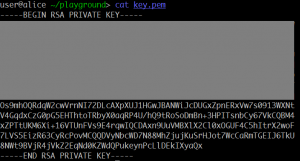
Here is a RSA private key with its upper part masked. Can your recover the private key and decrypt the file? equation.zip Summary: recovering RSA key from part of the private key.
Mar 13
0CTF 2016 Quals – RSA? (Crypto 2 pts)
It seems easy, right? rsa.zip Tip: openssl rsautl -encrypt -in FLAG -inkey public.pem -pubin -out flag.enc Summary: factoring 300-bit modulus into 3 primes, extracting cube roots.
Mar 07
Boston Key Party CTF 2016 – GCM (Crypto 9pts)
[8] : gsilvis counting magic – 9 – 4 solves : crypto: Here’s a verification/decryption server: gcm.ctf.bostonkey.party:32768 . Get the GCM MAC key (the thing the server prints out on startup). We’ve given you one valid ciphertext to get you started. It has iv: [102 97 110 116 97 115 116 105 99 32 105 …
Mar 07
Boston Key Party CTF 2016 – HMAC-CRC (Crypto 5pts)
[3] : hmac_crc – 5 – 36 solves : crypto: We’re trying a new mac here at BKP—HMAC-CRC. The hmac (with our key) of “zupe zecret” is ‘0xa57d43a032feb286’. What’s the hmac of “BKPCTF”? hmac-task.py Summary: breaking HMAC-CRC (again)
May 04
VolgaCTF Quals 2015 – CPKC (Crypto 400) writeup
cpkc A home-brewed cryptosystem, should be easy to break. Its keyspace seems to be rather large though… challenge.tar Summary: LLL-based attack on NTRUEncrypt-like cryptosystem.
Feb 09
Olympic CTF 2014 GuessGame (300)
Be careful, it’s cheating! nc 109.233.61.11 3126 Summary: discrete logarithm with group oracle
Feb 26
CodeGate 2012 Quals Forensic 500 Write-up
This file is Forensic file format which is generally used. Check the information of imaged DISK, find the GUIDs of every partition. Answer: strupr((part1_GUID) XOR (part2_GUID) XOR …) Download : B704361ACF90390C17F6103DF4811E2D Forensic 500 features EWF format container with EFI GPT partition table.
Feb 26
CodeGate 2012 Quals Vuln500 Write-up
1.234.41.7:22 ID : yesMan PWD : ohyeah123 Download vulnerable binary. Vuln500 was a hardened format-string vuln with ASLR, NX-stack, no-DTORs, RO .dynamic
Feb 26
CodeGate 2012 Quals Net400 Write-up
Because of vulnerability of site in Company A, database which contains user’s information was leaked. The file is dumped packet at the moment of attacking. Find the administrator’s account information which was leaked from the site. For reference, some parts of the packet was blind to XXXX. Answer : strupr(md5(database_name|table_name|decode(password_of_admin))) (‘|’is just a character) Download …
Feb 13
IFSF CTF #7 (X99) Write-up
this is one of their machines which have very sensitive informations , try to get for us the password 208.64.122.27 PORT : 3000 X99 carries a synthetic vulnerability that allows a char-by-char password bruteforce.
Feb 13
IFSF CTF Small Challenges (#4, #5, #6, #14, #15)
Contents #4 ER #5 Change #6 Call me #14 Seek me #15 Embedded docs