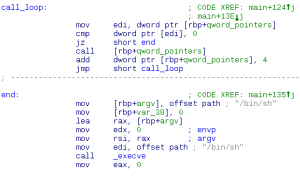
Play with this amazing calculator: calc.challenges.polictf.it:4000 Summary: Scheme eval
Tag: 2012
Nov 19
PoliCTF 2012 Crypto 500
Hensel and Gretel are looking for their new house, but the twisted seller who sold it to them decided to provide the coordinates to their new love nest only after ensuring that the couple is Smart enough to earn them. Thus, the seller provides them with the following map and leaves Hensel and Gretel to …
Nov 19
PoliCTF 2012 Crypto 200
Nov 19
PoliCTF 2012 Crypto 100
Since I needed to sign a document I thought about doing it with a Chinese paintbrush… Too bad my hand is not that steady, so just in case, I re-signed it with a common pen. Sadly I keep being forgetful, so I actually forgot where I left the two halves of the sigil I used …
Nov 13
Dobbertin Challenge 2012
The Dobbertin Challenge is issued every two years since 2006, in honor and memory of Prof. Hans Dobbertin. http://cryptochallenge.nds.rub.de:50080/ A simple JSON Web Service is provided, which processes PIN codes of users. A user can send his encrypted PIN to the Web Service, which decrypts and stores the PIN. The Web Service allows to use …
Nov 04
Hack.lu 2012 CTF Challenge #12 (500)
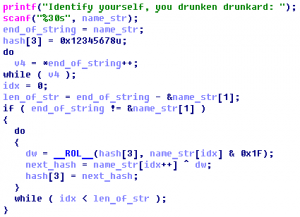
The famous zombie researcher “Donn Beach” almost created an immunization against the dipsomanie virus. This severe disease leads to the inability to defend against Zombies, later causes a complete loss of memory and finally turns you into one of them. Inexplicably Donn forgot where he put the license key for his centrifuge. Provide him a …
Oct 27
Hack.lu 2012 CTF Challenge #25 (200)
Heading up the steeple gave you and your companion a nice view over the outbreak situation in your city. But it also attracted a lot of unwanted attention. Zombies are surrounding your spot and are looking for an entrance to the building. You obviously need some bait to lure them away so you can flee …
Oct 26
Hack.lu 2012 CTF Challenge #3 (450)
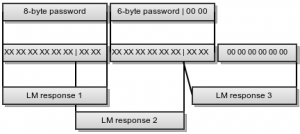
3 – Zombies like PPTP Our intel shows us that the Zombies use a MS-PPTP like protocol and luckily we could intercept a challenge-response transmission of one of the Zombie outposts. The important thing for Zombies in this war is mass! Not only brain mass but their mass. So they built their PPTP protocol compatible …
Oct 25
Hack.lu 2012 CTF Challenge #17 (400)
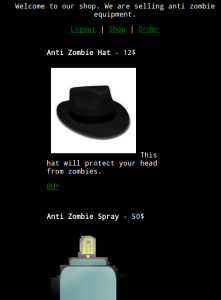
17 – Zombieshop A new company offers a lot of anti zombie equipment to protect yourself. Unfortunately not everyone can buy the good stuff. Only privileged users may do so. We managed to create an account, but it is not privileged. Your mission is to buy “Anti zombie Spray”. zomboy53:killthezombies https://ctf.fluxfingers.net:2077/ Summary: bruteforce DES
Oct 25
Hack.lu 2012 CTF Challenge #14-15 (150+250)
14 – Safehouse It’s the middle of the night. Nothing but complete darkness and the moaing of approaching zombies surrounds you. You need to escape. Fast. There seems to be nothing to hide and nowhere to run. But then – a small dancing gleam appears while you are running through the blackness. Could it be? …
Oct 25
Hack.lu 2012 CTF Challenge #7 (200)
7 – python jail You are surrounded by zombies. You heard there’s a safe house nearby, but climbing fences is hard with a beer belly. Thank god, there’s another surviver over there. “Hey! Help me!”, you shout. He just laughs and shakes you off the fence. Asshole. Later, you see his dead body lying in …
Oct 25
Hack.lu 2012 CTF Challenge #4 (250)
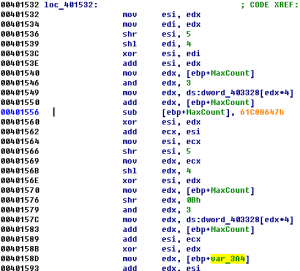
4 – Reduced Security Agency Some of our guys broke into the Reduced Security Agency and stole the source of their highly secure login system. Unfortunately no one of them made it uninfected back and so we only have a part of the source. Now it’s your turn to break their system and login to …
Oct 04
Announcing hackyou CTF
It’s fall already and that means the new CTF season is starting, and so is the new academic year in our university. This is the time when we want to attract more freshmen into our CTF tarpit ;-D So we are running – a CTF. But it’s not just for them. Wouldn’t it be fun …
May 01
SIMD [250] (Pirating)
After examining some code retrieved by our operative we are unsure whether it was written by an evil genius or a google employee. We will let you decide. Summary: linux x64 binary, obfuscated xor